@abucci@anthony.buc.ci see here in the okta docs: https://developer.okta.com/docs/reference/api/webfinger/ they are adding a prefix to the acct
so in effect it would look something like this:
---
subject: acct:me@sour.is
aliases:
- salty:me@sour.is
- yarn:xuu@ev.sour.is
- status:xuu@chaos.social
- mailto:me@sour.is
---
subject: salty:me@sour.is
aliases:
- acct:me@sour.is
links:
- rel: self
type: application/json+salty
href: https://ev.sour.is/inbox/01GAEMKXYJ4857JQP1MJGD61Z5
properties:
"http://salty.im/ns/nick": xuu
"http://salty.im/ns/display": Jon Lundy
"http://salty.im/ns/pubkey": kex140fwaena9t0mrgnjeare5zuknmmvl0vc7agqy5yr938vusxfh9ys34vd2p
---
subject: yarn:xuu@ev.sour.is
links:
- rel: https://txt.sour.is/user/xuu
properties:
"https://sour.is/rel/redirect": https://txt.sour.is/.well-known/webfinger?resource=acct%3Axuu%40txt.sour.is
---
subject: status:xuu@chaos.social
links:
- rel: http://joinmastodon.org#xuu%40chaos.social
properties:
"https://sour.is/rel/redirect": https://chaos.social/.well-known/webfinger?resource=acct%3Axuu%40chaos.social
---
subject: mailto:me@sour.is
...
@prologic@twtxt.net Unfortunately the RFC’s are a bit light in this regard. While it makes mention of different kinds of accounts like mailto: or status services.. it never combines them. It does make mention of using redirects to forward a request to other webfingers to provide additional detail.
I am kinda partial to using salty:acct:me@sour.is, yarn:acct:xuu@txt.sour.is, mailto:me@sour.is that could redirect to a specific service. and a parent account acct:me@sour.is that would reference them in some way. either in properties or aliases.
@prologic@twtxt.net That was exactly my thought at first too. but what do we put as the rel for salty account? since it is decentralized we dont have a set URL for machines to key off. so for example take the standard response from okta:
# http GET https://example.okta.com/.well-known/webfinger resource==acct:bob
{
"links": [
{
"href": "https://example.okta.com/sso/idps/OKTA?login_hint=bob#",
"properties": {
"okta:idp:type": "OKTA"
},
"rel": "http://openid.net/specs/connect/1.0/issuer",
"titles": {
"und": "example"
}
}
],
"subject": "acct:bob"
}
It gives one link that follows the OpenID login. So the details are specific to the subject acct:bob.
Mastodons response:
{
"subject": "acct:xuu@chaos.social",
"aliases": [
"https://chaos.social/@xuu",
"https://chaos.social/users/xuu"
],
"links": [
{
"rel": "http://webfinger.net/rel/profile-page",
"type": "text/html",
"href": "https://chaos.social/@xuu"
},
{
"rel": "self",
"type": "application/activity+json",
"href": "https://chaos.social/users/xuu"
},
{
"rel": "http://ostatus.org/schema/1.0/subscribe"
}
]
}
it supplies a profile page and a self which are both specific to that account.
Trying to wrap my head around webfinger..
my first thoughts about it were that a subject of acct:me@sour.is would have a listing of rel’s for the different accounts that are related to me (ie. yarn, salty, twitter, mastodon, etc…)
but maybe my thinking is at the wrong level.. that each of those accounts would be on a subject level and the rels are describing different aspects of that account. so i would have salty:acct:xuu@sour.is, twitter:acct:xuu, mastodon:acct:xuu@chaos.social, yarn:acct:xuu@ev.sour.is and then i could have a main acct:me@sour.is that links them together as aliases.
I found okta will do something similar with its accounts to show as okta:acct:user@domain so maybe I am on to something?
@prologic@twtxt.net What is the SMART reading for the disk?
@abucci@anthony.buc.ci did you know about the chip inside USB-C cables?

https://connectorsupplier.com/usb-type-c-what-you-need-to-know/
some groups have created their own chips that have hidden keyloggers that can phone home over network connections.
Interesting. Ive been using backupninja with Borg for snapshots.
Huh. I thought I had that one. Must be an unteste regression. Will add it to the list!
Did something chchange with how the discover feed is generated? My pods logout mode now only shows my twts. It used to be all twts from watcher observation like my logged on discover tab. @prologic@twtxt.net
An interesting read about testing code using nullable states instead of mocks.
https://www.jamesshore.com/v2/projects/testing-without-mocks/testing-without-mocks
@prologic@twtxt.net billionaires don’t exist. That many resources tied up by single individuals muck up the whole system.
@prologic@twtxt.net see where its used maybe that can help.
https://github.com/sour-is/ev/blob/main/app/peerfinder/http.go#L153
This is an upsert. So I pass a streamID which is like a globally unique id for the object. And then see how the type of the parameter in the function is used to infer the generic type. In the function it will create a new *Info and populate it from the datastore to pass to the function. The func will do its modifications and if it returns a nil error it will commit the changes.
The PA type contract ensures that the type fulfills the Aggregate interface and is a pointer to type at compile time.
@prologic@twtxt.net so basically you would use cgit + gitbug with some webhooks?
one that i think is pretty interesting is building up dependent constraints. see here.. it accepts a type but requires the use of a pointer to type.
https://github.com/sour-is/ev/blob/main/pkg/es/es.go#L315-L325
I am offended that you did not post your snarky twt.
I learned how to make gopls syntax highlight go templates in VSCodium.
By adding the following to my config
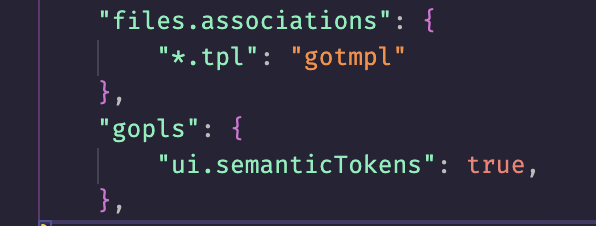
i could go from 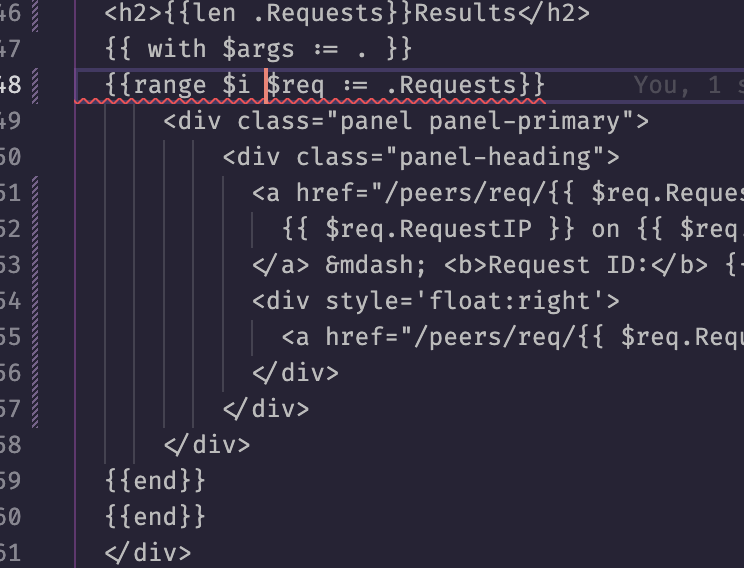 into
into 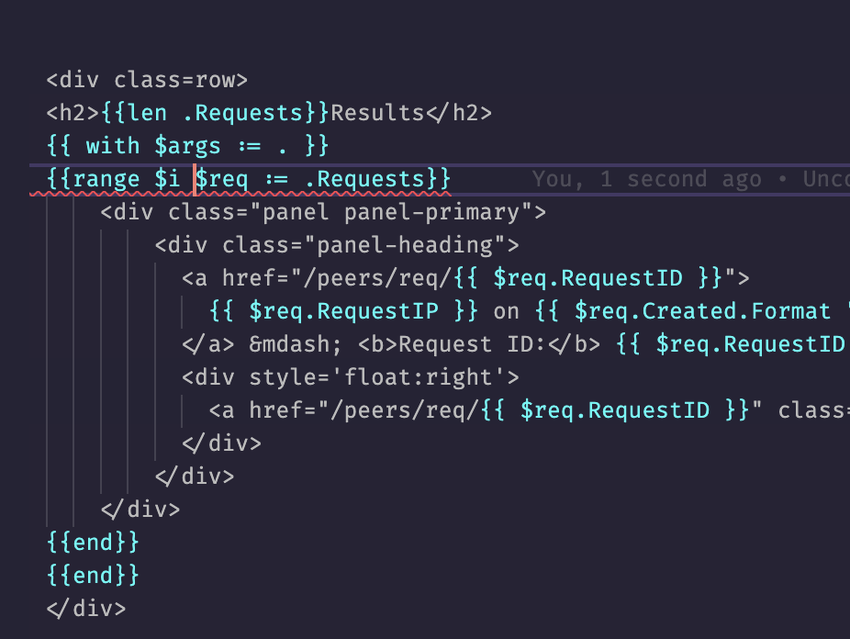
I’ll let the head of the bird site comment on that:

@prologic@twtxt.net its only a Pre-JR dev level.
@prologic@twtxt.net @justamoment@twtxt.net Yep, my back yard security cam. And my poor weather station buried in the snow.
A little late night visitor.
i added some disclaimers
Is it something to do with implicit declaration of printf?
@prologic@twtxt.net same.
$name$ and then dispatch the hashing or checking to its specific format.
I have submitted this to be used as the hash tooling for Yarn. See it as a good example on using this in a production environment!
@lyse@lyse.isobeef.org anyone willing to copy/paste security related things without understanding are gonna have a bad time.
Logged in using new argon2i password hash! 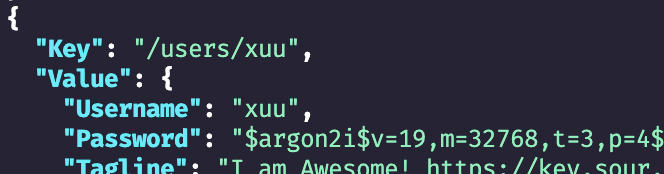
@lyse@lyse.isobeef.org Its just dead simple.. and others will salt which makes repeatability in examples a pain.
$name$ and then dispatch the hashing or checking to its specific format.
Circling back to the IsPreferred method. A hasher can define its own IsPreferred method that will be called to check if the current hash meets the complexity requirements. This is good for updating the password hashes to be more secure over time.
func (p *Passwd) IsPreferred(hash string) bool {
_, algo := p.getAlgo(hash)
if algo != nil && algo == p.d {
// if the algorithm defines its own check for preference.
if ck, ok := algo.(interface{ IsPreferred(string) bool }); ok {
return ck.IsPreferred(hash)
}
return true
}
return false
}
https://github.com/sour-is/go-passwd/blob/main/passwd.go#L62-L74
example: https://github.com/sour-is/go-passwd/blob/main/pkg/argon2/argon2.go#L104-L133
$name$ and then dispatch the hashing or checking to its specific format.
Hold up now, that example hash doesn’t have a
$prefix!
Well for this there is the option for a hash type to set itself as a fall through if a matching hash doesn’t exist. This is good for legacy password types that don’t follow the convention.
func (p *plainPasswd) ApplyPasswd(passwd *passwd.Passwd) {
passwd.Register("plain", p)
passwd.SetFallthrough(p)
}
https://github.com/sour-is/go-passwd/blob/main/passwd_test.go#L28-L31
$name$ and then dispatch the hashing or checking to its specific format.
Here is an example of usage:
func Example() {
pass := "my_pass"
hash := "my_pass"
pwd := passwd.New(
&unix.MD5{}, // first is preferred type.
&plainPasswd{},
)
_, err := pwd.Passwd(pass, hash)
if err != nil {
fmt.Println("fail: ", err)
}
// Check if we want to update.
if !pwd.IsPreferred(hash) {
newHash, err := pwd.Passwd(pass, "")
if err != nil {
fmt.Println("fail: ", err)
}
fmt.Println("new hash:", newHash)
}
// Output:
// new hash: $1$81ed91e1131a3a5a50d8a68e8ef85fa0
}
This shows how one would set a preferred hashing type and if the current version of ones password is not the preferred type updates it to enhance the security of the hashed password when someone logs in.
https://github.com/sour-is/go-passwd/blob/main/passwd_test.go#L33-L59
I made a thing. Its a multi password type checker. Using the PHC string format we can identify a password hashing format from the prefix $name$ and then dispatch the hashing or checking to its specific format.
how install gomodot? also.. @prologic@twtxt.net your domain has some pretty strong SEO mojo searching for install "gomodot" puts you on the google first page. 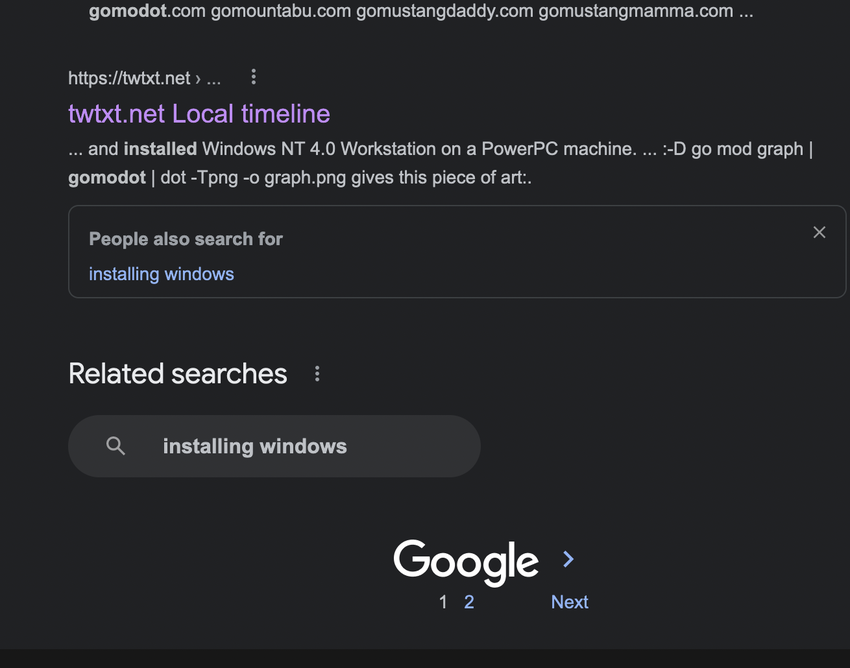
@lyse@lyse.isobeef.org im talking like some JS projects i have seen with 1-2G node_modules dirs. though yarn is quite vast in its modules because it does a LOOOOOOT of stuff in the background.
@carsten@yarn.zn80.net what type of NAS? I just upgraded my oooold (~2008) Drobo to a Synology. I have been impressed with all the neat stuff it can do.
@eaplmx@twtxt.net i used internet when it cost 13c per minute. my parents would get so mad if i went over the monthly base minutes CompuServe gave us.
@prologic@twtxt.net duud use an ad block on youtube.
(by the way Jesus is born end of September beginning of October)
or August… or Jun-July… or April.. hard to say really.
@prologic@twtxt.net ¯\_(ツ)_/¯
@prologic@twtxt.net “_foo_”
@prologic@twtxt.net “foo”
ahh this is useful https://go.dev/doc/modules/managing-dependencies. the go culture doesn’t typically have large dependency graphs like Ruby or JS.
@prologic@twtxt.net the go get and go mod tidy wont fetch new changes. that’s all a manual affair AFAIK
Ah git-bug! Ive chatted with the creator when he was working on the graphql parts. Its working with git objects directly sorta like how git-repo does code reviews. Its a pretty neat idea for storing data along side the branches. I believe they don’t add a disconnected branch to avoid data getting corrupted by merging branches or something like that.
He says “The college ready foundation send messages of support to all college ready foundation stations all around the world.”
It is a very odd message of support to themselves. But OK.
@prologic@twtxt.net.. hmm and now they are gone. :(
Twting to see if it will update my links list.
@prologic@twtxt.net I’m sure Monroe would like to know about them.