Microsoft Plans Smartphone-Style Permission Prompts for Windows 11 Apps
Microsoft is planning to bring smartphone-style app permission prompts to Windows 11, requiring apps to get explicit user consent before they can access sensitive resources like the file system, camera and microphone. The company’s Windows Platform engineer Logan Iyer said the move was prompted by applications increasingly overriding u … ⌘ Read more
eBay Bans Illicit Automated Shopping Amid Rapid Rise of AI Agents
EBay has updated its User Agreement to explicitly ban third-party “buy for me” agents and AI chatbots from interacting with its platform without permission. From a report: On its face, a one-line terms of service update doesn’t seem like major news, but what it implies is more significant: The change reflects the rapid emergence of what some are cal … ⌘ Read more
AI Agents ‘Perilous’ for Secure Apps Such as Signal, Whittaker Says
Signal Foundation president Meredith Whittaker warned that AI agents that autonomously carry out tasks pose a threat to encrypted messaging apps [non-paywalled source] because they require broad access to data stored across a device and can be hijacked if given root permissions.
Speaking at Davos on Tuesday, Whittaker said the deeper integrat … ⌘ Read more
Public Domain Day 2026 Brings Betty Boop, Nancy Drew and ‘I Got Rhythm’ Into the Commons
As the calendar flips to January 1, 2026, thousands of copyrighted works from 1930 are entering the US public domain alongside sound recordings from 1925, making them free to copy, share, remix and build upon without permission or licensing fees. The literary haul includes William Faulkner’s As I Lay D … ⌘ Read more
Apple Becomes a Debt Collector With Its New Developer Agreement
Apple released an updated developer license agreement this week that gives the company permission to recoup unpaid funds, such as commissions or any other fees, by deducting them from in-app purchases it processes on developers’ behalf, among other methods. From a report: The change will impact developers in regions where local law allows them to … ⌘ Read more
Lidar-Maker Luminar Files For Bankruptcy
Once a star of the self-driving hype cycle, lidar maker Luminar has filed for bankruptcy amid legal turmoil, layoffs, and a cooling autonomous-vehicle market. It plans to sell off its assets before shutting down entirely. The Verge reports: As part of its bankruptcy, Luminar is seeking permission to sell both its lidar and semiconductor businesses, the latter of which it has already agreed to … ⌘ Read more
The New York Times Is Suing Perplexity For Copyright Infringement
The New York Times is suing Perplexity for copyright infringement, accusing the AI startup of repackaging its paywalled reporting without permission. TechCrunch reports: The Times joins several media outlets suing Perplexity, including the Chicago Tribune, which also filed suit this week. The Times’ suit claims that “Perplexity provides commerci … ⌘ Read more
My file system when I try to edit a file without the proper permissions ⌘ Read more
Pope Francis’s Popemobile transformed into mobile clinic for Gaza children
A former “Popemobile” used by Pope Francis during his 2014 tour of the Holy Land has been transformed into a mobile health clinic for Gaza’s children, but Israeli authorities are yet to give permission for it to enter the war-ravaged strip. ⌘ Read more
Cloudflare Explains Its Worst Outage Since 2019
Cloudflare suffered its worst network outage in six years on Tuesday, beginning at 11:20 UTC. The disruption prevented the content delivery network from routing traffic for roughly three hours. The failure, writes Cloudflare in a blog post, originated from a database permissions change deployed at 11:05 UTC. The modification altered how a database query returned information about … ⌘ Read more
What’s your go-to strategy for giving engineers access to production?
I’ve been in this field for almost 15 years, and I don’t think I’ve ever seen two companies handle this the same way
Some other places just hand out just-in-time database access with short-lived credentials, others rely on rigid role-based permission, and others go all in on anonymized data dumps or shadow environments to avoid prod access altogether
What’s your go-to when it comes to giving access to engineers to access production app … ⌘ Read more
** The Access Control Apocalypse: How Broken Permissions Gave Me Keys to Every Digital Door**
Hey there😁
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/th … ⌘ Read more
Fluentd to Fluent Bit: A Migration Guide
Fluentd was created over 14 years ago and still continues to be one of the most widely deployed technologies for log collection in the enterprise. Fluentd’s distributed plugin architecture and highly permissive licensing made it ideal… ⌘ Read more
@bender@twtxt.net That is a noble goal. We can talk about that – as long as it doesn’t mean giving up essential freedoms like choosing which software you can run on your device (without having to ask someone for permission).
@aelaraji@aelaraji.com I use Alt+. all the time, it’s great. 👌
FWIW, another thing I often use is !! to recall the entire previous command line:
$ find -iname '*foo*'
./This is a foo file.txt
$ cat "$(!!)"
cat "$(find -iname '*foo*')"
This is just a test.
Yep!
Or:
$ ls -al subdir
ls: cannot open directory 'subdir': Permission denied
$ sudo !!
sudo ls -al subdir
total 0
drwx------ 2 root root 60 Jun 20 19:39 .
drwx------ 7 jess jess 360 Jun 20 19:39 ..
-rw-r--r-- 1 root root 0 Jun 20 19:39 nothing-to-see
i have been on a ROLL fixing server issues the other day i fixed my dead SFTP server which had a chroot permission issue
idfk where the error came from it just broke one day, maybe from one of my many server crashes which are becoming frequent and UGH i have to fix that too but i have a headache right now so one thing at a time. the error was ‘unexpected end of JSON input’ or something, for a while i thought oh permission error but turns out i can’t read the error that clearly indicated something syntax related (i did double check my env file though)
OpenAI doesn’t like it when you use “their” generated slop without permission
OpenAI says it has found evidence that Chinese artificial intelligence start-up DeepSeek used the US company’s proprietary models to train its own open-source competitor, as concerns grow over a potential breach of intellectual property. ↫ Cristina Criddle and Eleanor Olcott for the FT This is more ironic than writing a song called Ironic that lists situations that aren’t actually … ⌘ Read more
[ANN] Monero Remote Node Monitoring project updates
Since my last post on Reddit in June 2024, there have been some major changes and new features.
* updated the license from GLWTS to a more widely recognized and permissive one (BSD-3-Clause)
* UI: switched from SvelteKit to Templ+HTMX to reduce external dependencies
* added support for monitoring both IPv6 and I2P nodes
* set up a Tor Hidden service for the web UI
Links:
- GitHub repository
- [Website](https://xmr.d … ⌘ Read more
Kubernetes RBAC: improve the K8s security posture
Member post originally published on the Devtron blog by Siddhant Khisty TL;DR: Secure your Kubernetes cluster with Role-Based Access Control (RBAC) to define granular permissions for users and applications. This guide explains how to implement RBAC… ⌘ Read more
Docker Desktop 4.29: Docker Socket Mount Permissions in ECI, Advanced Error Management, Moby 26, and New Beta Features
Docker Desktop 4.29 introduces enhancements to secure and streamline the development process and to improve error management and workflow efficiency. With the integration of Enhanced Container Isolation (ECI) with Docker socket mount permissions, the debut of Moby 26 within Docker Desktop, and exciting features such as Docker Compose enhancements via synchronized file shares reaching Beta, we’re equipp … ⌘ Read more
Fix “warning: unable to access /Users/Name/.config/git/attributes Permission Denied” Errors
If you’re at the command line and perhaps interacting with Homebrew, Git, or similar, you may run into an error message that says something like the following “warning: unable to access /Users/Name/.config/git/attributes” : Permission denied”. This error message sounds more alarming than it is in most cases, but regardless, you likely want to fix … ⌘ Read more
@lyse@lyse.isobeef.org its a hierarchy key value format. I designed it for the network peering tools i use.. I can grant access to different parts of the tree to other users.. kinda like directory permissions. a basic example of the format is:
@namespace
# multi
# line
# comment
root :value
# example space comment
@namespace.name space-tag
# attribute comments
attribute attr-tag :value for attribute
# attribute with multiple
# lines of values
foo :bar
:bin
:baz
repeated :value1
repeated :value2
each @ starts the definition of a namespace kinda like [name] in ini format. It can have comments that show up before. then each attribute is key :value and can have their own # comment lines.
Values can be multi line.. and also repeated..
the namespaces and values can also have little meta data tags added to them.
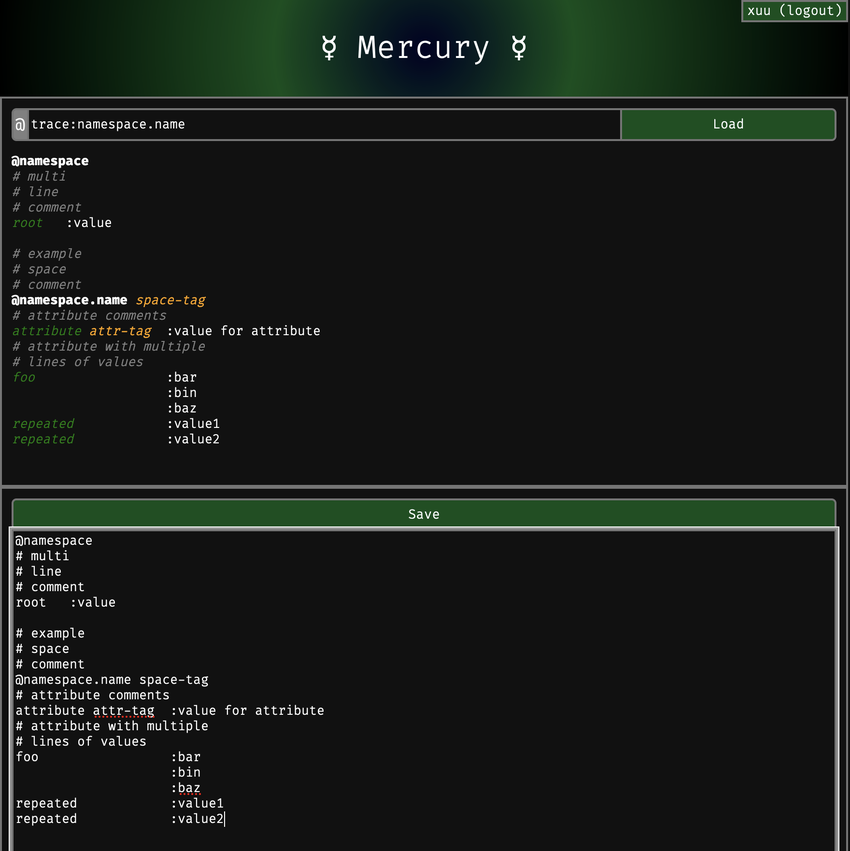
the service can define webhooks/mqtt topics to be notified when the configs are updated. That way it can deploy the changes out when they are updated.
# ssh -p 2222 cas.run help
The authenticity of host '[cas.run]:2222 ([139.180.180.214]:2222)' can't be established.
RSA key fingerprint is SHA256:i5txciMMbXu2fbB4w/vnElNSpasFcPP9fBp52+Avdbg.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[cas.run]:2222' (RSA) to the list of known hosts.
abucci@cas.run: Permission denied (publickey).
So you would have:
type ErrPermissionNotAllowed []Permission
func (perms ErrPermissionNotAllowed) Is(permission Permission) bool {
for _, p := range perms {
if p == permission { return true }
}
return false
}
var err error = errPermissionNotAllowed{"is-noob"}
if errors.Is(err, ErrPermissionNotAllowed{}) { ... } // user is not allowed
var e ErrPermissionNotAllowed
if errors.As(err, e) && e.Is("a-noob") { ... } // user is not allowed because they are a noob.
You can have Error return just “permission not allowed” if the array is empty. It would print the same as the first.
New tool to secure your GitHub Actions
Introducing a new tool to monitor and control the permissions of the repository token for GitHub Actions. ⌘ Read more
Design’s journey towards accessibility
Design can have a significant impact on delivering accessible experiences to our users. It takes a cultural shift, dedicated experts, and permission to make progress over perfection in order to build momentum. We’ve got a long way to go, but we’re starting to see a real shift in our journey to make GitHub a true home for all developers. ⌘ Read more
Looks like Google’s using this blog post of mine without my permission. I hate this kind of tech company crap so much.
in deontic logic, is ~obligation(~x)=permission(x)?
New npm features for secure publishing and safe consumption
Now you can create tokens with fine-grained permissions for automating your publishing and organization management workflows. And a new code explorer allows you to view content of a package directly in the npm portal. ⌘ Read more
Prosodical Thoughts: Bringing FASTer authentication to Prosody and XMPP
As our work continues on modernizing XMPP authentication,
we have some more new milestones to share with you. Until now our work has
mostly been focused on internal Prosody improvements, such as the new roles\
and permissions framework. Now we are starting to extend our
work to the actual client-to-server protocol in XMPP.
Prosody and [Snikket](https://snik … ⌘ Read more
Huh… Nope.
HTTP/1.1 200 OK
Content-Length: 407
Content-Type: text/calendar
Access-Control-Allow-Origin: *
Access-Control-Expose-Headers: ETag
Permissions-Policy: interest-cohort=()
Content-Security-Policy: default-src 'none'; sandbox
Referrer-Policy: same-origin
Vary: Authorization
BEGIN:VCALENDAR
VERSION:2.0;2.0
PRODID:SandCal
CALSCALE:GREGORIAN
BEGIN:VEVENT
DTSTAMP:20220822T180903Z
UID:bb63bfbd-623e-4805-b11b-3181d96375e6
DTSTART;TZID=America/Chicago:20220827T000000
CREATED:20220822T180903Z
LAST-MODIFIED:20220822T180903Z
LOCATION:https://meet.jit.si/Yarn.social
SUMMARY:Yarn Call
RRULE:FREQ=WEEKLY
DTEND;TZID=America/Chicago:20220827T010000
END:VEVENT
END:VCALENDAR
More than 10 journalists denied permission to cover Hong Kong handover anniversary events due to security reasons, reporters’ group says
Post photographer among those denied permission to cover celebratory events on July 1. Other rejected applicants include photographer from Information Services Department and journalists from Reuters and Agence France-Press. ⌘ Read more
Monal IM: Monal 5.0.1: Synchronized builds and bugfixes
We have released Monal in version 5.0.1 which contains mostly corrections and small improvements. Now the iOS and macOS builds are also synchronized and available in the Apple App Store.
Here are the changes in this release:
- Show warning if camera permissions are missing while trying to use camera
- Fixed duplication … ⌘ Read more
Only in Belgium : Was the built without planning permission? ⌘ Read more…
added some pages on #permissive #publicdomain licenses that I often reach for: !CC0 and !unlicense.
Impact Is Now Free & Open Source
My HTML5 Game Engine Impact launched almost 8 years ago. The last update was published in 2014. While Impact still works nicely in modern browsers, it lacks support for better graphic and sound APIs that are now available. I felt increasingly bad for selling a product that is hardly maintained or improved.
So as of today Impact will be available completely for free, published under the permissive MIT License.
Impact’s source is available on [gith … ⌘ Read more
Seek permission, not forgiveness · Nick Sweeney https://nicksweeney.com/2007/09/08/seek-permission-not-forgiveness/
Nix logo
Long overdue, the Nix project finally has a logo!
The logo was originally created by Simon Frankau for the Haskell\
logo competition, who kindly gave us permission to use it
for the Nix project. (The snowflake motif is even more
appropriate for Nix, because nix is Latin for
snow.) Any further modifications are entirely our
fault. ⌘ Read more