**WooCommerce Users Beware: Fake Patch Phishing Campaign Unleashes Site Backdoors **
Imagine this: you’re running your WooCommerce store, sipping coffee ☕, and an urgent email lands in your inbox. It scr … ⌘ Read more
** JWT, Meet Me Outside: How I Decoded, Re-Signed, and Owned the App **
Hey there!😁
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/jwt-meet-me-outside-how-i-decoded-re-signed-and-owned-the-app-95791eabcf5d? … ⌘ Read more
**Hackers Exploit Craft CMS Flaws: A Deep Dive into CVE-2025–32432 **
Imagine running a sleek website powered by Craft CMS, only to discover that hackers have slipped through the digital backdoor, wreaking…
[Continue reading on Info … ⌘ Read more
$300 Google Cloud Free Trial: Create Your First VM
Non-members can read this article for free using this link.
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/300-google-cloud-free-trial-create-your-first-vm-5a12b6821b0f?source=r … ⌘ Read more
**Master Spring Boot APIs Like a Pro: Skills That Distinguish Good Developers from Great Ones **
In the fast-moving world of backend development, it’s no longer enough to … ⌘ Read more
Mastering Java Records: The Ultimate Guide to Cleaner, Faster, and Immutable Code
Introduction
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/mastering-java-records-the … ⌘ Read more
** Microsoft Fortifies MSA Signing Infrastructure with Azure Confidential VMs After Storm-0558…**
In the ever-evolving cyber threat landscape, 2023 saw one of the most talked-ab … ⌘ Read more
** CloudImposer: How a Malicious PyPI Package Could’ve Hijacked Google Cloud Composer**
In early 2025, a critical vulnerability in Google Cloud Platform’s (GCP) Cloud Composer service came to light, … ⌘ Read more
**DslogdRAT Malware: A Sneaky Cyberattack Exploiting Ivanti ICS Zero-Day **
Buckle up, cybersecurity enthusiasts! 🚀 A new villain has entered the digital stage: DslogdRAT, a stealthy malware that’s been causing…
[Continue r … ⌘ Read more
Free Resources to Learn PenTesting in 2025 ⌘ Read more
Trinity Desktop Environment R14.1.4 released
The Trinity Desktop Environment, the modern-day continuation of the KDE 3.x series, has released version R14.1.4. This maintenance release brings new vector wallpapers and colour schemes, support for Unicode surrogate characters and planes above zero (for emoji, among other things), tabs in kpdf, transparency and other new visual effects for Dekorator, and much more. TDE R14.1.4 is already available for a variety of Linux distributions, and c … ⌘ Read more
Deals: M4 MacBook Air from $849, M3 iPad Air from $499, AirPods 4 for $99, Apple Watch 10 for $299, & More
Amazon is offering some really fantastic deals on Apple products right now, bringing the M4 MacBook Air to the lowest price available yet at $150 off retail, cutting $100 off the price of the M3 iPad Air models, taking $100 off the price of Apple Watch Series 10, and some whopper discounts on AirPods 4, … [Read More](https://osx … ⌘ Read more
7 to 12 and use the first 12 characters of the base32 encoded blake2b hash. This will solve two problems, the fact that all hashes today either end in q or a (oops) 😅 And increasing the Twt Hash size will ensure that we never run into the chance of collision for ions to come. Chances of a 50% collision with 64 bits / 12 characters is roughly ~12.44B Twts. That ought to be enough! -- I also propose that we modify all our clients and make this change from the 1st July 2025, which will be Yarn.social's 5th birthday and 5 years since I started this whole project and endeavour! 😱 #Twtxt #Update
We have 4 clients but this should be 6 I believe with tt2 from @lyse@lyse.isobeef.org and Twtxtory from @javivf@adn.org.es?
☁️How to Setup a Custom Subdomain on xss.ht — A Complete Hacker’s Guide
Free Article Link
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/%EF%B8%8Fhow-to-setup-a-custom-subdom … ⌘ Read more
SEH Exploitation Overflow — Vulnserver GMON ⌘ Read more
How to Install a Honeypot to Catch Hackers ⌘ Read more
Vaulting over a .innerHTML sink in a Locked-Down CSP ⌘ Read more
$500 Bounty: For a Simple Open Redirect
How a Language Chooser Flaw Led to Open Redirect and Server Issues on HackerOne
From SOAP to Shell: Exploiting Legacy SOAP Services for Full Admin Account Takeover (And Nearly… ⌘ Read more
** Login? Who Needs That? Bypassing OAuth Like a Lazy Hacker on Sunday ☀️**
Free Link🎈
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/login-who-needs-that-bypassing-oauth-like-a- … ⌘ Read more
** How to Turn Cybersecurity Into a Full-Time Income (My Blueprint)**
💡Free Article Link
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/how-to-turn-cybersecurity-into-a-full-time-income-my-blueprint-f4d70 … ⌘ Read more
The Hacker’s Library: Uncovering the Best Books ⌘ Read more
** Rack::Static Vulnerability Exposes Ruby Servers to Data Breaches! **
Hold onto your keyboards, Ruby developers! 😱 A critical security flaw in the Rack::Static middleware has been uncovered, potentially…
[Continue reading on InfoS … ⌘ Read more
AnalogLamb Expands Maple Series with Low-Cost ESP32C6 Breakout Boards
AnalogLamb has introduced three new RISC-V development boards based on the ESP32-C6, designed for low-cost, full-function, and low-power IoT applications. These boards feature Espressif’s first Wi-Fi 6 SoC, integrating Wi-Fi 6 (2.4 GHz), Bluetooth 5 LE, and IEEE 802.15.4 protocols. Each board is built around the ESP32-C6-WROOM-1 module, which combines a high-performance 32-bit RISC-V core […] ⌘ Read more
Can you automate the drawing with a script? On X11, you can:
#!/bin/sh
# Position the pointer at the center of the dot, then run this script.
sleep 1
start=$(xdotool getmouselocation --shell)
eval $start
r=400
steps=100
down=0
for step in $(seq $((steps + 1)) )
do
# pi = 4 * atan(1)
new_x=$(printf '%s + %s * c(%s / %s * 2 * (4 * a(1)))\n' $X $r $step $steps | bc -l)
new_y=$(printf '%s + %s * s(%s / %s * 2 * (4 * a(1)))\n' $Y $r $step $steps | bc -l)
xte "mousemove ${new_x%%.*} ${new_y%%.*}"
if ! (( down ))
then
xte 'mousedown 1'
down=1
fi
done
xte 'mouseup 1'
xte "mousemove $X $Y"
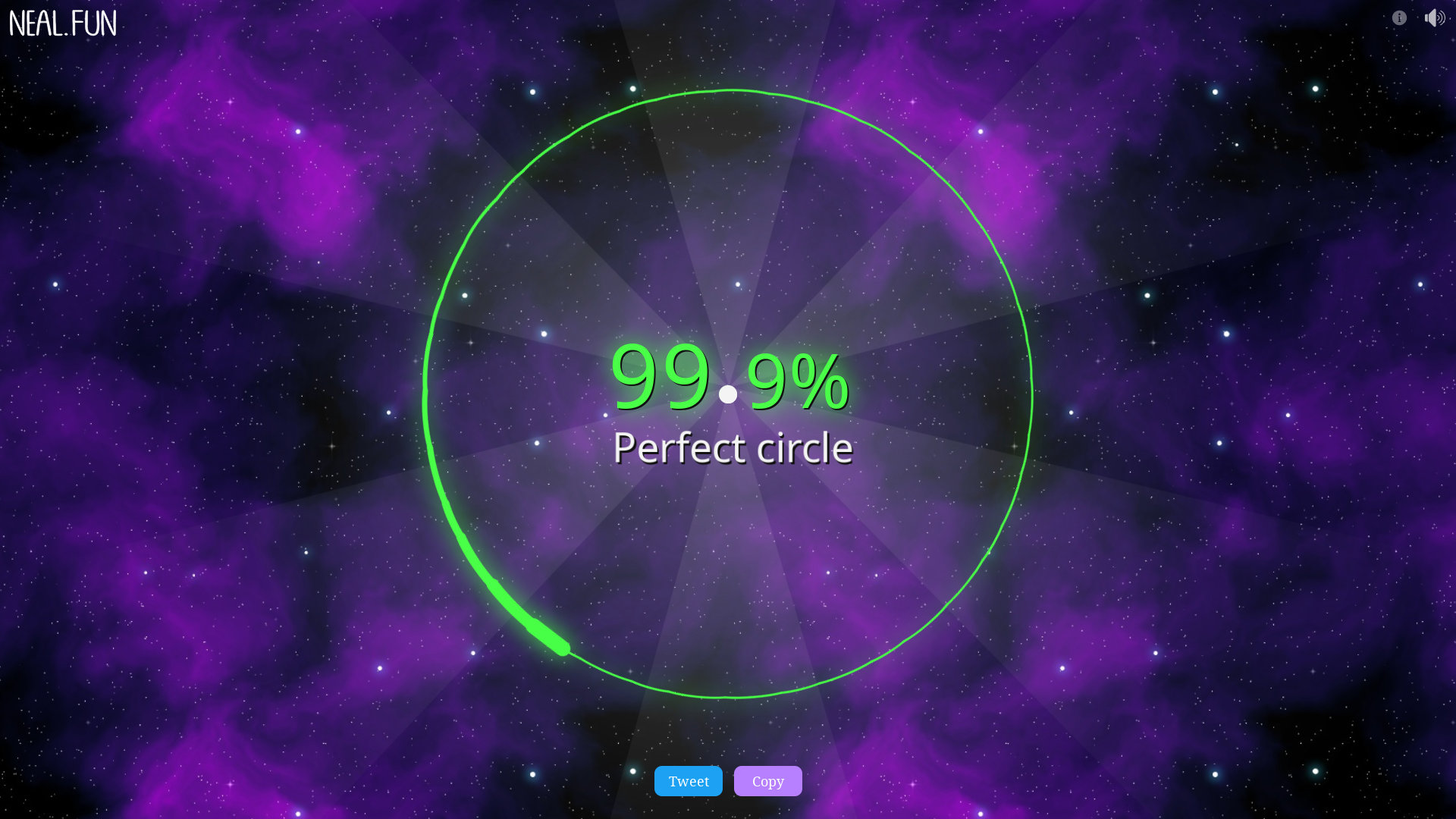
Interestingly, you can abuse the scoring system (not manually, only with a script). Since the mouse jumps to the locations along the circle, you can just use very few steps and still get a great score because every step you make is very accurate – but the result looks funny:
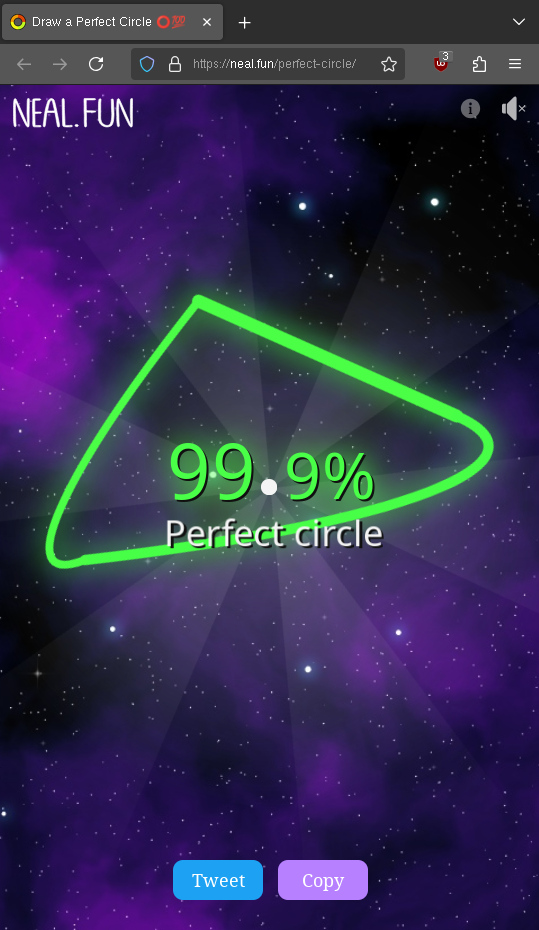
🥴
⏱️ There were no visible errors, no hints… only the server’s hesitation told me the truth.
It didn’t scream. It whispered… and I heard it.
[Continue reading on I … ⌘ Read more
**Path Traversal Attack: How I Accessed Admin Secrets **
Path Traversal Attack: How I Accessed Admin Secrets 📂
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/path-traversal-attack-how-i-accessed-admin-secrets-fa5de1865031?source … ⌘ Read more
Top 5 Open Source Tools to Scan Your Code for Vulnerabilities
These tools help you find security flaws in your code before attackers do.
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/top-5-open-source-tools-to-s … ⌘ Read more
Pinellas County - 4 miles: 4.01 miles, 00:08:20 average pace, 00:33:27 duration
moved this to today since tomorrow we have to wake up early and drive to TN. half a pizza and two pints sloshing around still felt okay. the pepperoni definitely gave me some additional heartburn though!
#running
NUCLEO-WBA65RI Brings Bluetooth LE, Thread, and Zephyr RTOS to STM32 Nucleo-64 Platform
The NUCLEO-WBA65RI is a wireless STM32 Nucleo-64 development board built around the STM32WBA65RIV7 microcontroller. It combines the MB2130 MCU RF board with the MB1801 mezzanine board to support Bluetooth LE and IEEE 802.15.4-based protocols such as Thread, Matter, and Zigbee. The STM32WBA65RIV7 microcontroller is a 32-bit Arm Cortex-M33 device featuring 2 MB of flash and … ⌘ Read more
Fluent Bit v4.0: Celebrating new features and 10th anniversary
The Fluent Bit maintainers have exciting news to share! Fluent Bit version 4 is out and just in time to celebrate the project’s 10-year anniversary. The journey: From embedded logging to multi-Signal observability With over 15… ⌘ Read more
4 weeks after adoption and she finally felt safe enough to get on the couch with me! ⌘ Read more
LitmusChaos at KubeCon + CloudNativeCon Europe 2025: A Recap
The cloud native community recently converged in London from April 1 – 4, 2025, for an incredible edition of KubeCon + CloudNativeCon Europe. From our perspective at LitmusChaos, it was a week filled with inspiring sessions,… ⌘ Read more
Administrator | HackTheBox ⌘ Read more
**The Fastest Way to Learn Web Hacking in 2025 (With Free Resources) **
🔓Free Article Link
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/the-fastest-way-to-learn-web-hacking-in-2025-with-free-resourc … ⌘ Read more
Hidden Tricks to Spot Phishing Emails Before They Trick You!
Phishing emails are like traps set by cybercriminals to trick you into sharing personal details, clicking dangerous links, or downloading…
[Continue reading on InfoSec Write-ups … ⌘ Read more
** Hostile Host Headers: How I Hijacked the App with One Sneaky Header **
Hey there!😊
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/hostile-host-headers-how-i-hijacked-the-app-with-one-sneaky-hea … ⌘ Read more
Unrestricted Access to All User Information | REST API Oversharing ⌘ Read more
GitLab CI for Python Developers: A Complete Guide
Automating Testing, Linting, and Deployment for Python projects using GitLab CI/CD
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/gitlab-ci-for-python-developers-a-complete-guide-83794cb91 … ⌘ Read more
Beetle RP2350 is a $4.90 Mini Development Board for Embedded Projects
The Beetle RP2350 is a coin-sized development board designed for space-constrained embedded projects. Despite its compact 25 × 20.5 mm footprint, it offers a wide range of hardware features and low power consumption, enabling its use in portable devices such as retro computers, game consoles, lighting controllers, and electronic badges. This board is built around […] ⌘ Read more
** How I discovered a hidden user thanks to server responses ?**
My first real step into web hacking and it wasn’t what i thought it would be.
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/how-i-discovered-a-hidde … ⌘ Read more
PNPT Exam Review — 2025 ⌘ Read more
How to Build a Threat Detection Pipeline from Scratch (Like a Cyber Ninja!)
Hey, cyber fam! Have you ever asked yourself:
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/how-to-build-a-threat … ⌘ Read more
Nothing changed… except for one detail. And that was enough to hack
Sometimes, hacking doesn’t require any exploit… just good observation.
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/nothing-c … ⌘ Read more
Email Verification Bypass during Account Creation | Insecure Design ⌘ Read more
How to Create a Botnet Using One Tool: A Proof of Concept for Educational Purposes Aspiring…
Learn how attackers build and control botnets — safely and ethically — using … ⌘ Read more
**Burp, Bounce, and Break: How Web Cache Poisoning Let Me Control the App **
Hey there!😁
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/burp-bounce-and-break-how-web-cache-poisoning-let-me-con … ⌘ Read more
OWASP Juice Shop | Part 2 — Bully Chatbot ⌘ Read more
OWASP Juice Shop | Part 1 — ScoreBoard Solution — StrawHat Hackers ⌘ Read more