Copy vim in byobu on server to local clipboard with big file? ⌘ Read more
The Atlantic: Trump ‘fumed’ over Ukraine’s drone strikes on Russian military airfields ⌘ Read more
Russia offers political asylum to Elon Musk over Trump feud ⌘ Read more
I Let ChatGPT Make All My Architectural Decisions for a Month: The Surprising Results
Comments ⌘ Read more
Trump and Musk: The Break-Up ⌘ Read more
During a massive attack in Kyiv, a man in the metro was holding his cat’s paw the whole time. ⌘ Read more
What are you doing this weekend?
Feel free to tell what you plan on doing this weekend and even ask for help or feedback.
Please keep in mind it’s more than OK to do nothing at all too! ⌘ Read more
ICE officers stuck in Djibouti shipping container with deported migrants ⌘ Read more
Am I a Shark or Am I a Cat ⌘ Read more
Ukraine’s defence forces strike two Russian airbases overnight – Ukraine’s General Staff, photos, videos ⌘ Read more
Russian missiles, drones target Kyiv, Ternopil, Lutsk in one of Moscow’s largest air assaults, civilians killed and injured (updates) ⌘ Read more
10 Incredibly Specific Oreo Facts You’ll Think About at 2 A.M.
You’ve twisted them, dunked them, and crumbled them into milkshakes—but odds are, you don’t really know Oreos. Behind the world’s best-selling cookie is a labyrinth of marketing manipulation, food science secrets, and flavor experiments so bizarre they’re hidden from the public. These aren’t your standard “Oreo was invented in 1912” trivia tidbits. These are the […]
The post [10 Incredibly Specific Oreo Facts … ⌘ Read more
Ukraine to Receive More IRIS-T Missile Systems From Germany ⌘ Read more
I can do this all day ⌘ Read more
I Learned Rust In 24 Hours To Eat Free Pizza Morally
This is a satirical tech story. For readers who prefer the text version, it’s provided below.
I Learned Rust in 24 Hours to Eat Free Pizza Morally
This is not just a story about pizza. As a recent Phoronix article explains,
the Linux Rust subsystem got into major drama because of my humble quest.
Well, here’s my side of the story, with every kernel of truth exposed.
A Moral Quest for Pizza
Des … ⌘ Read more
Create own Hacking SERVER Instead of Portswigger exploit server
This article describes about to create your own server that helps to exploit CORS vulnerability or more.
[Continue reading on InfoSec Write-ups »](https://i … ⌘ Read more
OIDC: The Fellowship of the Token (Part III)
One token to rule them all, one token to find them, One token to bring them all, and in the cluster spawn them (I meant the pods.).
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/oidc-the-fellowsh … ⌘ Read more
How I Hacked 100+ Accounts Using Just XSS
One Small Flaw, 100+ Accounts Stolen — Here’s How It Happened
Part 3: How to Become a Pentester in 2025:Practical Practice: Labs & CTFs ⌘ Read more
** The “Unlimited Leave” Hack I Found at My College** ⌘ Read more
next-20250606: linux-next
Version:next-20250606 (linux-next)Released:2025-06-06 ⌘ Read more
How Simple RECON Earned Me ₹XX,000 at Zerodha ⌘ Read more
Russian weapons plant hit by drones in Tambov Oblast, media reports attacks across country ⌘ Read more
This might be the end
How a Welcome Email Can Be Used for Malicious Redirection
Free Article Link: Click for free!
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/how-a-welcome-email-can-be-used-for-malicious-redirection-fd833ec71550? … ⌘ Read more
A Step-by-Step Plan to Secure Web Backends with XAMPP (Part 1/3)
Installing and Configuring XAMPP
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/a-step-by-step-plan-to-secure-web-backends-with-xampp-p … ⌘ Read more
** Broken Object Fiesta: How I Used IDOR, No Auth, and a Little Luck to Pull User Data **
Hey there!😁
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/broken-object-fiest … ⌘ Read more
Self-hosting your own media considered harmful according to YouTube
Article URL: https://www.jeffgeerling.com/blog/2025/self-hosting-your-own-media-considered-harmful
Comments URL: https://news.ycombinator.com/item?id=44197932
Points: 517
# Comments: 190 ⌘ Read more
Honest Government Ads | News, Bloopers & Behind the Scenes ⌘ Read more
Morse Micro and Gateworks Launch Wi-Fi HaLow Solution for Industrial Connectivity
Morse Micro and Gateworks Corporation have partnered to bring Wi-Fi HaLow (IEEE 802.11ah) to industrial environments. In collaboration with Silex Technology, they offer a hardware and software ecosystem for long-range, low-power, and secure wireless networking across manufacturing, energy, and transportation sectors. Wi-Fi HaLow operates in the sub-GHz frequency band, offering a co … ⌘ Read more
Our babies are obsessed with their new bed. ⌘ Read more
This is my carefully cared-for kitten, whom I saved from the brink of death. ⌘ Read more
Trump administration imposes sanctions on four ICC judges in unprecedented move ⌘ Read more
ICE officers stuck in Djibouti shipping container with deported migrants ⌘ Read more
Our girl Turtle turned 20 today! ⌘ Read more
I’ll love you forever, Tom. ⌘ Read more
Rare black iceberg spotted off Labrador coast could be 100,000 years old, prof says ⌘ Read more
Neighbor-Source Heat Pump
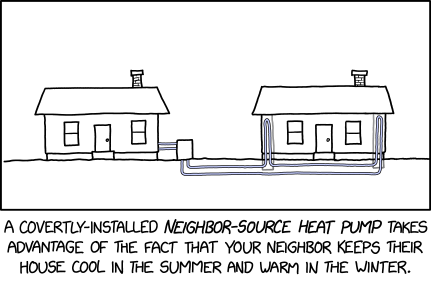 ⌘ Read more
⌘ Read more
JMP: Mitigating MITMs in XMPP
In October 2023, Jabber.ru, “the largest Russian XMPP messaging service”, discovered that both Hetzner and Linode had been targeting them with Machine-In-The-Middle (MITM) attacks for up to 6 months. MITM attacks are when an unauthorised third party intercepts traffic intended for someone else. At the point of interception, the attacker can inspect and even modify that traffic. TLS was created to mitigate this; all communication between the two parties is encrypted, so the third party sees … ⌘ Read more