My cow is 2.3kg at 4 years old. ⌘ Read more
Avoid #each_with_object (generally)
Comments ⌘ Read more
My dog(female) found this little guy all alone in the middle of my yard after a rain. He was wet, cold and sneeze but now he is showing of he’s mighy roar. Say hi to little 1month year old Mufasa ⌘ Read more
Build and Run Your Own FreeBSD-native Containers with Buildah, Containerfiles and Podman
Comments ⌘ Read more
Introducing vim-dan Plugin “Documents And Notes” ⌘ Read more
GitHub for Beginners: Building a React App with GitHub Copilot
Follow along and build a frontend client using React and Copilot Chat.
The post GitHub for Beginners: Building a React App with GitHub Copilot appeared first on The GitHub Blog. ⌘ Read more
I just want to share pics of my baby🐈 ⌘ Read more
Please open your heart. ⌘ Read more
next-20250512: linux-next
Version:next-20250512 (linux-next)Released:2025-05-12 ⌘ Read more
What are you doing this week?
What are you doing this week? Feel free to share!
Keep in mind it’s OK to do nothing at all, too. ⌘ Read more
I leave here my stray cat’s lovely purr, and my breath sound 😅 ⌘ Read more
10 Popular Songs That Are Surprisingly About Drugs
Nothing is better than a good love song or an upbeat summer hit, but sometimes those songs’ meanings can be quite deceiving. There is an endless supply of popular songs that are clearly about drugs, but some are not quite so obvious. From artists like Ed Sheeran to TLC, these artists have released music that […]
The post [10 Popular Songs That Are Surprisingly About Drugs](https://listverse.com/2025/05/12/10-popular-songs-that-are … ⌘ Read more
Compress-a-thon — CSP Bypass via Redirection — Pentathon 2025
Compress-a-thon is a “web exploitation” challenge that was featured in Pentathon 2025 Finale Jeopardy CTF Round. This challenge involved…
[Continue reading on InfoSec Write-ups »](https://inf … ⌘ Read more
SSRF via PDF Generator? Yes, and It Led to EC2 Metadata Access
👨💻Free Article Link
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/ssrf-via-pdf-generator-yes-and-it-led-to-ec2-metadata-access-39b8e5b41840 … ⌘ Read more
Shadow Credentials in Active Directory: When the Exploit Doesn’t Work — Until It Does ⌘ Read more
**The Hidden Language: Exploiting GraphQL for Unauthorized Data Dump **
Free Link🎈
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/the-hidden-language-exploiting-graphql-for-unauthorized-data-dump-8 … ⌘ Read more
Bug Hunting in JS Files: Tricks, Tools, and Real-World POCs
✅Free Article Link
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/bug-hunting-in-js-files-tricks-tools-and-real-world-pocs-b4d43dd41d8e?source=rss—-7 … ⌘ Read more
Bug Bounty Race: Exploiting Race Conditions for Infinite Discounts ⌘ Read more
**Top 5 Easiest Bugs for Beginners in Bug Bounty **
Top 5 Easiest Bugs for Beginners in Bug Bounty 🐞
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/top-5-easiest-bugs-for-beginners-in-bug-bounty-45dd81c49e03?source=rss—-7b722bfd1b8d- … ⌘ Read more
$10,000 Bounty: HackerOne Report Comments Leak via “Export as .zip”
How a new export feature unintentionally exposed private discussions in limited disclosure reports
[Continue reading on InfoSec Write-ups »](https://infose … ⌘ Read more
Understanding Stealer Logs and Their Role in Security Testing: A Focus on Asset Discovery- Part 2 ⌘ Read more
Understanding Stealer Logs and Their Role in Security Testing — Part 1 ⌘ Read more
API Key Exposure in NASA GitHub Repository Leads to Unauthorized Access to Academic Data
🔓Free Article Link
[Continue reading on InfoSec Write-ups »](https://infosecwriteu … ⌘ Read more
Subdomain Takeover: My $450 Win & How You Can Do It Too
Free Article Link: Click for free!
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/subdomain-takeover-my-450-win-how-you-can-do-it-too-3337ca0513b6?source=rss—-7b722 … ⌘ Read more
Celebrating my first fur-mother’s day. Thank you for making me a fur-mom my baby ⌘ Read more
How I Found SSTI in a Search Bar ⌘ Read more
How Backups Can Break End-to-End Encryption (E2EE) ⌘ Read more
Hidden HackerOne & Bugcrowd Programs: How to Get Private Invites
“Private programs are where the real gold lies… but no one tells you how to get there. Let me break it down for you — with secrets most…
[Continue reading on In … ⌘ Read more
Goodbye, my best little friend, I hope we meet again. ⌘ Read more
He was found on the side of the road, dirty, hungry and scared ⌘ Read more
Fifty years of poppy growing in Tasmania
The push for pharmaceuticals to combat diabetes and weight loss is leading to a revival of the poppy industry in Tasmania. ⌘ Read more
He thinks I can’t see him ⌘ Read more
Meet my new kitten 🐱 ⌘ Read more
Deposition
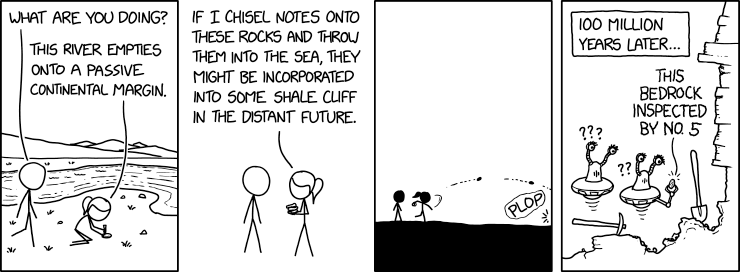 ⌘ Read more
⌘ Read more
I’ve been adpoted ⌘ Read more
6.15-rc6: mainline
Version:6.15-rc6 (mainline)Released:2025-05-11Source:linux-6.15-rc6.tar.gzPatch:full ( incremental) ⌘ Read more