Mozilla Lawsuit from Former Executive Gets Jury Trial Date
The former “CEO-to-be” will get his day in court against the Firefox maker… but not until a few months after Mozilla loses 80%+ of their revenue. ⌘ Read more
anon1337 proposes bounty for haveno-ts Dart port
anon13371 has proposed a bounty2 for porting the Haveno TypeScript Library 3 to Dart:
Total Bounty: 0 XMR (to date)
No specific details (requirements/deliverables) were provided for this bounty.
To start working on the task yourself, you should make your intentions public by posting a comment in the bounty’s thread.
To increase the bounty you can transfer some XMR to the address posted by the … ⌘ Read more
[ANN] Istanbul meetup sponsored by WizardSwap.io, organised by OrangeFren.com
- Date: Friday the 20th of December 2024 @ 18:00 local time
- Location: CoBAC Workshop, Sarıdemir, Ragıp Gümüşpala Cd. No:29, 34116 Fatih/İstanbul, Türkiye
- Tickets: free
Link: https://orangefren.com/event/20
orangefren.com ⌘ Read more
b4n6_b4n6 proposes bounties for Stack Wallet bug fixes
b4n6_b4n61 has proposed bounties2’3 for fixing two recently reported Stack Wallet4 issues5:
#1 Add checksum check for mnemonic seed
Total Bounty: 0.5 XMR (to date)
#2 Diagnose and fix linux crash
Total Bounty: 0.5 XMR (to date)
To start working on the tasks yourself, you should make your intentions public by posting a comment in the bounty threads.
To increase the bounties you can … ⌘ Read more
[ANN] RandomX 5 Year Anniversary
Yes, it’s been 5 years on the same PoW. And the date came and went without much fanfare. For those perhaps trickling into monero because of the pRiCe, you may not be aware of how much of a milestone this is in the context of an industry that is ruthless when it comes to exploiting weak PoW algorithms for profit.
Link: https://farside.link/libreddit/r/Monero/comments/1h6e4nk/
gingeropolous (Reddit) ⌘ Read more
An insider look at how we schedule KubeCon + CloudNativeCon events across the globe
CNCF Event Venue & Date Selection Process Planning a large conference like KubeCon + CloudNativeCon Europe or North America is a complex endeavor that begins years in advance. The venue and date selection process is an… ⌘ Read more
ProcessOne: Docker: set up ejabberd and keep it updated automagically with Watchtower
This blog post will guide you through the process of setting up an ejabberd Community Server using Docker and Docker Compose, and will also introduce Watchtower for automatic updates. This approach ensures that your configuration remains secure and up to date.
Furthermore, we will examine the potential risks associated with automatic updates and suggest Diun as an alternative tool for notification-based up … ⌘ Read more
MoneroKon 2025 event to be held June 20-22 in Prague at La Fabrika/Second Culture
The fifth edition of the Monero Konferenco 1 annual meeting is set2 to take place place in Prague, Czech Republic on June 20-22 at the La Fabrika/Second Culture 3 venue (previously known as Paralelni Polis):
Save the date: MoneroKon will be held 20th - 22nd June 2025 [..] Sign up to our mailing list to be notified when tickets go on sale
The previous conference was also held in Pragu … ⌘ Read more
[ANN] Searching for more Monerotopia24 hackers
The hackathon will occur all 4 days of the Conference in the TERRACE/LOFT of the Venue, Huerto Roma Verde, BUT we do have a house dedicated to the Hackers for those interested in rooming with the hackers BUT we only have 1 spot left in the house! So please reach out asap if interested in that spot!
Date: November 14-17th
Location: TERRACE/LOFT area in MoneroTopia24 Confer in Huerto Roma Verde, Mexico City
Links:
MoneroKon proposes bounty for Monero POS Android app
MoneroKon1 has proposed a bounty2 for the creation of a FOSS Monero Android app3 that can be used by merchants on a dedicated POS PDA device with thermal printer:
The aim is to make in-person transactions easy and fast at events such as MoneroKon.
Total Bounty: 0 XMR (to date)
@Codebuzz@www.codebuzz.nl Speed is an issue for the client software, not the format itself, but yes I agree that it makes the most sense to append post to the end of the file. I’m referring to the definition that it’s the first url = in the file that is the one that has to be used for the twthash computation, which is a too arbitrary way of defining something that breaks treading time and time again. And this is the case for not using url+date+message = twthash.
[ANN] Nicosia meetup sponsored by WizardSwap.io, organised by OrangeFren.com
- Date: Friday the 1st of November 2024 @ 18:00 local time
- Location: Axess Workspace, 28, Konstantinou Palaiologou 1015, Nicosia, Cyprus
- Tickets: free
Link: https://orangefren.com/event/19
orangefren.com ⌘ Read more
Dilli Hai Dilwalon Ki
(Translation: “Delhi is for the warm-hearted”) A Delhi guide by Kunal Kushwaha, Field CTO at Civo The capital city of India, Delhi, has roots that trace back thousands of years. Known as Indraprastha in ancient texts dating as… ⌘ Read more
[ANN] MoneroTalk #329: Why Tornado Cash free speech defense was rejected in court
Date/Time: 24/10/17 at 7AM-EDT/1PM-CEST
Links:
monerotalk.live ⌘ Read more
https://strftime.org/ date format
[ANN] Monero Meetup in Mexico City with Doug of MoneroTalk/Monerotopia on Sun, Oct 13th at 11AM!
Date/Time: Sun, Oct 13th at 11AM
Location: Cardinal Casa de Café (Córdoba 132, Roma Nte., Cuauhtémoc, 06100 Ciudad de México)
Link: https://farside.link/libreddit/r/Monerotopia/comments/1fw6q8t/
monerotalk.live ⌘ Read more
@bender@twtxt.net It’s the experience of an ordinary person in a strange place where memories are disappearing with the help of the Memory Police. The setting feels contemporary (to the book’s 1994 publication date) rather than futuristic, except for some unexplained stuff about memories.
(#2024-09-24T12:45:54Z) @prologic@twtxt.net I’m not really buying this one about readability. It’s easy to recognize that this is a URL and a date, so you skim over it like you would we mentions and markdown links and images. If you are not suppose to read the raw file, then we might a well jam everything into JSON like mastodon
Some more arguments for a local-based treading model over a content-based one:
The format:
(#<DATE URL>)or(@<DATE URL>)both makes sense: # as prefix is for a hashtag like we allredy got with the(#twthash)and @ as prefix denotes that this is mention of a specific post in a feed, and not just the feed in general. Using either can make implementation easier, since most clients already got this kind of filtering.Having something like
(#<DATE URL>)will also make mentions via webmetions for twtxt easier to implement, since there is no need for looking up the#twthash. This will also make it possible to make 3th part twt-mentions services.Supporting twt/webmentions will also increase discoverability as a way to know about both replies and feed mentions from feeds that you don’t follow.
I demand full 9 digit nano second timestamps and the full TZ identifier as documented in the tz 2024b database! I need to know if there was a change in daylight savings as per the locality in question as of the provided date.
@sorenpeter@darch.dk I like this idea. Just for fun, I’m using a variant in this twt. (Also because I’m curious how it non-hash subjects appear in jenny and yarn.)
URLs can contain commas so I suggest a different character to separate the url from the date. Is this twt I’ve used space (also after “replyto”, for symmetry).
I think this solves:
- Changing feed identities: although @mckinley@twtxt.net points out URLs can change, I think this syntax should be okay as long as the feed at that URL can be fetched, and as long as the current canonical URL for the feed lists this one as an alternate.
- editing, if you don’t care about message integrity
- finding the root of a thread, if you’re not following the author
An optional hash could be added if message integrity is desired. (E.g. if you don’t trust the feed author not to make a misleading edit.) Other recent suggestions about how to deal with edits and hashes might be applicable then.
People publishing multiple twts per second should include sub-second precision in their timestamps. As you suggested, the timestamp could just be copied verbatim.
@movq@www.uninformativ.de I did started from scratch, today. I using am commit 6e8ce5afdabd5eac22eae4275407b3bd2a167daf (HEAD -> main, origin/main, origin/HEAD), I keep myself up-to-date, LOL. Still, that specific twtxt (o6dsrga) is no longer.
This is how my original message shows up on jenny:
From: quark <quark>
Subject: (#o) @prologic this was your first twtxt. Cool! :-P
Date: Mon, 16 Sep 2024 12:42:27 -0400
Message-Id: <k7imvia@twtxt>
X-twtxt-feed-url: https://ferengi.one/twtxt.txt
(#o) @<prologic https://twtxt.net/user/prologic/twtxt.txt> this was your first twtxt. Cool! :-P
Hmm… I replied to this message:
From: prologic <prologic>
Subject: Hello World! 😊
Date: Sat, 18 Jul 2020 08:39:52 -0400
Message-Id: <o6dsrga>
X-twtxt-feed-url: https://twtxt.net/user/prologic/twtxt.txt
Hello World! 😊
And see how the hash shows… Is it because that hash isn’t longer used?
Release Date for iOS 18, macOS Sequoia, iPadOS 18, is September 16
In all of the hubbub about the new iPhone 16 series and release candidate builds for macOS Sequoia, iOS 18, and iPadOS 18, you might have missed when Apple announced what the official release dates will be for all of their new operating systems. Let’s clear that up right now so that you can be … Read More ⌘ Read more
I was not suggesting to that everyone need to setup a working webfinger endpoint, but that we take the format of nick+(sub)domain as base for generating the hashed together with the message date and content.
If we omit the protocol prefix from the way we do things now will that not solve most of the problems? In the case of gemini://gemini.ctrl-c.club/~nristen/twtxt.txt they also have a working twtxt.txt at https://ctrl-c.club/~nristen/twtxt.txt … damn I just notice the gemini. subdomain.
Okay what about defining a prefers protocol as part of the hash schema? so 1: https , 2: http 3: gemini 4: gopher ?
@prologic@twtxt.net Some criticisms and a possible alternative direction:
Key rotation. I’m not a security person, but my understanding is that it’s good to be able to give keys an expiry date and replace them with new ones periodically.
It makes maintaining a feed more complicated. Now instead of just needing to put a file on a web server (and scan the logs for user agents) I also need to do this. What brought me to twtxt was its radical simplicity.
Instead, maybe we should think about a way to allow old urls to be rotated out? Like, my metadata could somehow say that X used to be my primary URL, but going forward from date D onward my primary url is Y. (Or, if you really want to use public key cryptography, maybe something similar could be used for key rotation there.)
It’s nice that your scheme would add a way to verify the twts you download, but https is supposed to do that anyway. If you don’t trust https to do that (maybe you don’t like relying on root CAs?) then maybe your preferred solution should be reflected by your primary feed url. E.g. if you prefer the security offered by IPFS, then maybe an IPNS url would do the trick. The fact that feed locations are URLs gives some flexibility. (But then rotation is still an issue, if I understand ipns right.)
yarnd that's been around for awhile and is still present in the current version I'm running that lets a person hit a constructed URL like
@prologic@twtxt.net What? I compiled, updated, and restarted. If you check what my pod reports, it gives that 7a… SHA. I don’t know what that other screenshot is showing but it seems to be out of date. That was the SHA I was running before this update.
As we reach mid-year 2024, a look at CNCF, Linux Foundation, and top 30 open source project velocity
Staff post by Chris Aniszczyk Date/Time: July 11 at 8am For the last several years we have tracked open source project velocity, which has enabled us to monitor the trends and technologies that resonate with developers and end… ⌘ Read more
What is retrieval-augmented generation, and what does it do for generative AI?
Here’s how retrieval-augmented generation, or RAG, uses a variety of data sources to keep AI models fresh with up-to-date information and organizational knowledge.
The post What is retrieval-augmented generation, and what does it do for generative AI? appeared first on [T … ⌘ Read more
Hi @movq@www.uninformativ.de, is it better now?
I have put in a psudo twthash since I did not archive from a specific date/post, but just what I did not find relevant to keep in my main feed.
How to Hide the Clock at MacOS Login Screen
The Mac login screen and lock screen displays a prominent large clock, with the date and time visible over the wallpaper or screensaver. While many users appreciate having the time and date right there at the login screen, other users may wish to hide the clock, date, and time, from the MacOS login screen. If … Read More ⌘ Read more
Apple Cancels the Apple Car Project
Apple has canceled their ambitious decade-long car project, codenamed Project Titan, according to a report from Bloomberg. Development on the Apple Car, which was apparently intended to be an electric vehicle with self-driving capabilities, became news in 2015, and originally had a speculative release dates of 2019 and 2020, which obviously came and went without … Read More ⌘ Read more
‘A lot of contentious issues on the agenda’: Australia and China preparing for high-level talks
Details and dates are still to be determined and announced, but experts say a range of thorny issues could be on the table. ⌘ Read more
GitHub Copilot Enterprise is now generally available
Our most advanced AI offering to date is customized to your organization’s knowledge and codebase, infusing GitHub Copilot throughout the software development lifecycle.
The post GitHub Copilot Enterprise is now generally available appeared first on The GitHub Blog. ⌘ Read more
Sad to see moc removed from the official arch linux repos, but also cool to learn the debian project has been quietly patching it and keeping it up to date in recent years. Long live the music on console player. (And debian!) :-)
“You know who makes very good sandwiches? Felix! Did you ever taste his cream cheese and pimento on date-nut bread?” #nowplaying
Add Corporate Earnings Reports to Your Calendar on Mac, iPhone, iPad via Stocks App
The Stocks app for iPhone, Mac, and iPad, now offers a super convenient way of knowing when a companies upcoming earnings reports will be, and, even better for you earnings season enthusiasts, you can add those earnings report dates directly to your calendar immediately from the Stocks app. Because who doesn’t love listening in on … [Read More](https://osxdaily.com/2024 … ⌘ Read more
Do you know if all your repositories have up-to-date dependencies?
Consider deploying the GitHub Action: Evergreen so that you know each of your repositories are leveraging active dependency management with Dependabot.
The post Do you know if all your repositories have up-to-date dependencies? appeared first on The GitHub Blog. ⌘ Read more
Anyone else noticed how the current date and the climate are more resembling Blade Runner each year.
XMPP Providers: XMPP Providers Fully Automated
Automate all the ThingsDuring the past year, the team behind the XMPP Providers project worked on automating the process of gathering data about XMPP providers.
Automating this process reduces manual work significantly (for example, checking websites by hand, verifying information, listing sources, etc.) and helps to sustain the team’s efforts.
Automation also enables the project to be up to date – every day!
[ … ⌘ Read more
@movq@www.uninformativ.de
Yes I have threading on. I wanted to put new posts at the top with set sort_aux = reverse-last-date-sent but that that makes the threads do the newest first not bellow the reply. So all replies are in a top newest order. But I can just use sort date_sent and then go to the end to go to the newest post.
Should we remove best-before dates on produce?
Advocates say a simple change would stop Australian households from unwittingly throwing out perfectly edible food, and they are banding together to get the regulator on board. ⌘ Read more
How to Use & Access GPT-4 for Free
You may already be using ChatGPT, the phenomenally powerful and useful AI tool, but the free version is based on GPT-3.5. GPT-4 is said to be ten times more advanced, with enhanced creativity, reliability, up-to-date information, and an ability to interpret more nuanced instructions, so it’s understandable why users would like to explore and experience … Read More ⌘ Read more
How to Use & Access GPT-4 for Free
You may already be using ChatGPT, the phenomenally powerful and useful AI tool, but the free version is based on GPT-3.5. GPT-4 is said to be ten times more advanced, with enhanced creativity, reliability, up-to-date information, and an ability to interpret more nuanced instructions, so it’s understandable why users would like to explore and experience … Read More ⌘ Read more
@eapl.me@eapl.me are ISPs still injecting code into HTTP in this the year 2023? I remember getting notices that my comcast modem is out of date pushed into websites back a decade ago.
Date Line
 ⌘ Read more
⌘ Read more
@abucci@anthony.buc.ci my last experience with it was with a Debian package which is known for being out of date :-D
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
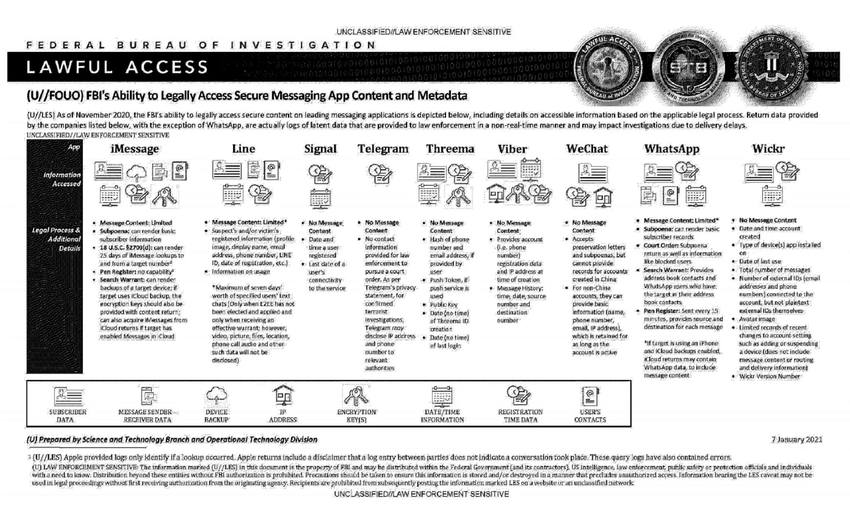
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
** summer’s lease hath all too short a date **
After the excitement of last summer I was hopeful for a chill one this year. So far, so good.
We visited the island where we used to live and started our family. We saw a few friends, and visited some fa … ⌘ Read more