podman works with TLS. It does not have the "--docker" siwtch so you have to remove that and use the exact replacement commands that were in that github comment.
@prologic@twtxt.net what do you mean when you say “Docker API”? There are multiple possible meanings for that. podman conforms to some of Docker’s APIs and it’s unclear to me which one you say it’s not conforming to.
You just have to Google “podman Docker API” and you find stuff like this: https://www.redhat.com/sysadmin/podman-rest-api
What is Podman’s REST API?Podman’s REST API consists of two components:
- A Docker-compatible portion called Compat API
- A native portion called Libpod API that provides access to additional features not available in Docker, including pods
Or this: https://docs.podman.io/en/latest/markdown/podman-system-service.1.html
The REST API provided by podman system service is split into two parts: a compatibility layer offering support for the Docker v1.40 API, and a Podman-native Libpod layer.
GitHub Copilot Chat beta now available for every organization
All GitHub Copilot for Business users now have access to a limited GitHub Copilot Chat beta, bringing the power of conversational coding right to the IDE. ⌘ Read more
Erlang Solutions: How IoT is Revolutionising Supply Chain Management
As global supply chains continue to face significant disruptions, many businesses are turning to IoT to access greater visibility, reactivity, and streamlined operations.
Unforeseen geopolitical conflicts, economic pressures due to inflation and severe climate change events have all contributed to an uncertain and cost … ⌘ Read more
Isode: Icon-PEP 2.0 – New Capabilities
Icon-PEP is used to enable the use of IP applications over HF networks. Using STANAG 5066 Link Layer as an interface.
Listed below are the changes brought in with 2.0.
Web ManagementA web interface is provided which includes:
- Full configuration of Icon-PEP
- TLS (HTTPS) access and configuration including bootstrap with self signed certificate and ide … ⌘ Read more
(De)coding conventions
Navigating the ebb and flow of programming paradigms–from the shifts in the JavaScript ecosystem and TypeScript’s rise, to AI’s role in advancing accessibility, and strategies for encouraging non-code contributions–tune in to the latest episode of The ReadME Podcast for more. ⌘ Read more
Accessibility considerations behind code search and code view
A look at how we improved the readability of code on GitHub. ⌘ Read more
Introduction to SELinux
SELinux is the most popular Linux Security Module used to isolate and protect system components from one another. Learn about different access control systems and Linux security as I introduce the foundations of a popular type system. ⌘ Read more
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
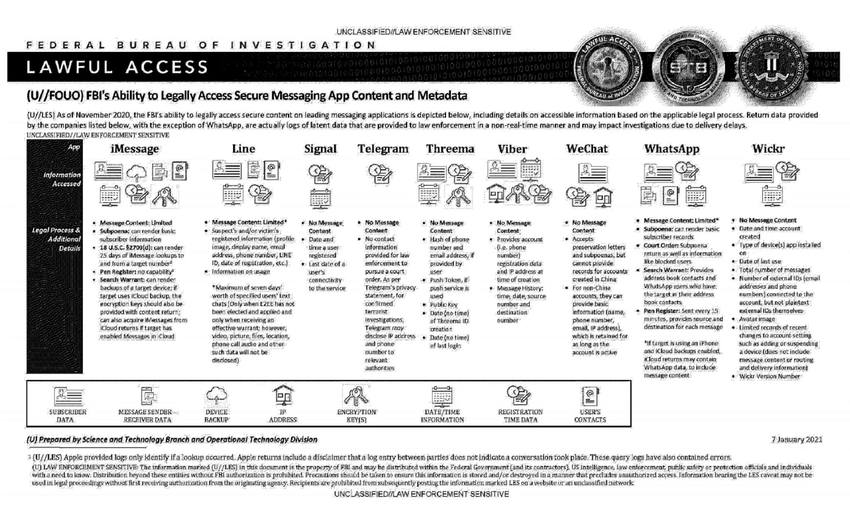
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
Isode: Harrier 3.3 – New Capabilities
Harrier is our Military Messaging client. It provides a modern, secure web UI that supports SMTP, STANAG 4406 and ACP 127. Harrier allows authorised users to access role-based mailboxes and respond as a role within an organisation rather than as an individual.
 that my eyes can’t see normally. That feels very much like rudimentary augmented reality that an appropriately-designed headset could mostly automate. VR/AR/metaverse isn’t there yet, but it seems at least possible for the hardware and software to develop accessibility features that would make it workable for low vision people.
@stigatle@yarn.stigatle.no @prologic@twtxt.net @eldersnake@we.loveprivacy.club I love VR too, and I wonder a lot whether it can help people with accessibility challenges, like low vision.
But Meta’s approach from the beginning almost seemed like a joke? My first thought was “are they trolling us?” There’s open source metaverse software like Vircadia that looks better than Meta’s demos (avatars have legs in Vircadia, ffs) and can already do virtual co-working. Vircadia developers hold their meetings within Vircadia, and there are virtual whiteboards and walls where you can run video feeds, calendars and web browsers. What is Meta spending all that money doing, if their visuals look so weak, and their co-working affordances aren’t there?
On top of that, Meta didn’t seem to put any kind of effort into moderating the content. There are already stories of bad things happening in Horizon Worlds, like gangs forming and harassing people off of it. Imagine what that’d look like if 1 billion people were using it the way Meta says they want.
Then, there are plenty of technical challenges left, like people feeling motion sickness or disoriented after using a headset for a long period of time. I haven’t heard announcements from Meta that they’re working on these or have made any advances in these.
All around, it never sounded serious to me, despite how much money Meta seems to be throwing at it. For something with so much promise, and so many obvious challenges to attack first that Meta seems to be ignoring, what are they even doing?
How we work: inclusive retrospectives for the GitHub Accessibility leadership team
Learn about tools and processes the GitHub Accessibility leadership team uses for retrospectives that fully engage every team member. ⌘ Read more
Building a more inclusive GitHub Global Campus
Every student and teacher deserves the same access to GitHub Education offerings. We’ve enlisted GitHub’s Accessibility team to help identify areas for improving inclusivity. ⌘ Read more
They haven’t written the federation code yet. Its literally run on the staging instance. People are paying to access the alpha. Though if you want a code to see what all the fuss is about there are a few with invites around here.
There is a “right” way to make something like GitHub CoPilot, but Microsoft did not choose that way. They chose one of the most exploitative options available to them. For that reason, I hope they face significant consequences, though I doubt they will in the current climate. I also hope that CoPilot is shut down, though I’m pretty certain it will not be.
Other than access to the data behind it, Microsoft has nothing special that allows it to create something like CoPilot. The technology behind it has been around for at least a decade. There could be a “public” version of this same tool made by a cooperating group of people volunteering, “leasing”, or selling their source code into it. There could likewise be an ethically-created corporate version. Such a thing would give individual developers or organizations the choice to include their code in the tool, possibly for a fee if that’s something they want or require. The creators of the tool would have to acknowledge that they have suppliers–the people who create the code that makes their tool possible–instead of simply stealing what they need and pretending that’s fine.
This era we’re living through, with large companies stomping over all laws and regulations, blatantly stealing other people’s work for their own profit, cannot come to an end soon enough. It is destroying innovation, and we all suffer for that. Having one nifty tool like CoPilot that gives a bit of convenience is nowhere near worth the tremendous loss that Microsoft’s actions in this instace are creating for everyone.
**RT by @mind_booster: 1/3 🚨Recent @POLITICOEurope leak revealed that US & EU officials have agreed to cooperate on measures to turn public opinion against #encryption.
Experts’ statements by @edri & @globalencrypt have called out against this plan
➡️https://edri.org/our-work/eu-us-plan-offensive-to-legitimise-police-access-to-data-civil-society-responds-amid-growing-fears-press-release/
➡️https://www.globalencryption.org/2023/04/statement-on-eu-us-cooperation-against-encryption/**
1/3 🚨Recent [@POLITICOEurope](https … ⌘ Read more
I’m not super a fan of using json. I feel we could still use text as the medium. Maybe a modified version to fix any weakness.
What if instead of signing each twt individually we generated a merkle tree using the twt hashes? Then a signature of the root hash. This would ensure the full stream of twts are intact with a minimal overhead. With the added bonus of helping clients identify missing twts when syncing/gossiping.
Have two endpoints. One as the webfinger to link profile details and avatar like you posted. And the signature for the merkleroot twt. And the other a pageable stream of twts. Or individual twts/merkle branch to incrementally access twt feeds.
Docker and Hugging Face Partner to Democratize AI
We’re excited to announce that Happy Face and Docker are partnering to democratize AI and make it more accessible to software engineers! ⌘ Read more
GitHub celebrates the ingenuity of developers with disabilities in new video series
Learn how developers with disabilities are pushing the boundaries of accessibility with ingenuity, open source, and generative AI on The ReadME Project. ⌘ Read more
‘Game-changer’ deal sees Australian avocados to set sail for India
A free-trade agreement and access to the Indian market of 1.5 billion people is being hailed as “the light at the end of the tunnel” for avocado growers following a recent avo “glut”. ⌘ Read more
How to use your own domain as your BlueSky handle
I recently got access to the BlueSky beta, and decided to poke around to see what it’s all about. I will save the details of what it is and how I feel about it for a different post. However, one of the first things you do when you sign up is choose a username that exists under the bsky.app domain. I have zero interest in another name rush where everyone tries to claim the shortest username possible, so I went with aaronpk.bsky.app rather than trying to get a … ⌘ Read more
GitHub Security Lab audited DataHub: Here’s what they found
The GitHub Security Lab audited DataHub, an open source metadata platform, and discovered several vulnerabilities in the platform’s authentication and authorization modules. These vulnerabilities could have enabled an attacker to bypass authentication and gain access to sensitive data stored on the platform. ⌘ Read more
** Ideas for making accessibility and equity a core part of the software development lifecycle **
In accessibility and the product person I said
we need to make accessibility a core part of our processes
Here, I want to talk about that in more detail. I want to briefly explore what making accessibility a part of core processes looks like, and how that is different from centering access … ⌘ Read more
** Accessibility and the product person **
This post is a slightly modified version of a talk I presented to the product practice at my work. It presents a few ways that product designers and managers can help to move accessibility forward. It is a little bit different than what I normally share, here, but, I thought it may be interesting to some folks.
[ gateway and on end-to-end encryption around pubsub.
Oh, and if everything goes well, this blog post should be accessible from XMPP and ActivityPub (and HTTP and ATOM feed), using the same identifier goffi@goffi.org.
The work made on the AP gateway has been possible thanks to a NLnet/NGI0 grant (w … ⌘ Read more