Erlang Solutions: The Diversity & Inclusion Programme: Our Pledge
As technology becomes increasingly integrated into our lives, the minds behind it must come from diverse backgrounds. Different viewpoints lead to better solutions, ensuring that the tech we create addresses the needs of a global audience.
At Erlang Solutions, we believe that a diverse workforce is a catalyst for creativity and progress. By sponsoring the Diversity & Inclusion Programme for [Code BEAM events](https://codebeameurope … ⌘ Read more
Explain infrastructure as code (alternatives to IaC)
Member post originally published on AppCD’s blog by Kunal Dabir I was recently speaking with an SRE who, when asked for their opinion on Infrastructure as Code (IaC), shouted, “it’s terrible and our devs hate it!” Now we… ⌘ Read more
Found means fixed: Secure code more than three times faster with Copilot Autofix
With Copilot Autofix, developers and security teams can keep new vulnerabilities out of code and confidently remediate their backlog security debt.
The post Found means fixed: Secure code more than three times faster with Copilot Autofix appeared first on [The GitHub … ⌘ Read more
yeah its the same dude.
This project is verrrry alpha. all the configuration is literally in the code.
From object transition to RCE in the Chrome renderer
In this post, I’ll exploit CVE-2024-5830, a type confusion in Chrome that allows remote code execution (RCE) in the renderer sandbox of Chrome by a single visit to a malicious site.
The post From object transition to RCE in the Chrome renderer appeared first on The GitHub Blog. ⌘ Read more
Python Bans Prominent Dev for Enjoying the Wrong SNL Sketch
Even worse: He was too active in a conversation. That’s a Code of Conduct Violation! ⌘ Read more
Getting to know the new CNCF Code of Conduct Committee
By the CNCF Code of Conduct Committee Hello CNCF community! Our permanent CNCF Code of Conduct Committee has been operating for eight months, so it’s time for us to share information about incidents we’ve handled in our community… ⌘ Read more
How to use AI coding tools to learn a new programming language
Explore how AI coding tools like GitHub Copilot can accelerate your journey to learn new programming languages.
The post How to use AI coding tools to learn a new programming language appeared first on [The GitHub Blog](https://gi … ⌘ Read more
The technical complexities of decoupled authorization
Member post originally published on the Cerbos blog by James Walker Decoupling authorization from your main application code makes authorization more scalable, easier to maintain, and simpler to integrate with your components. However, these benefits are difficult to… ⌘ Read more
The XMPP Standards Foundation: The XMPP Newsletter July 2024
XMPP Newsletter Banner
Welcome to the XMPP Newsletter, great to have you here again!
This issue covers the month of July 2024.
If you are interested to join the XMPP Standards Foundation as a member, please apply until August 18th, 2024!.
XMPP and Google Summer of Code 2024… ⌘ Read more
Erlang Solutions: Erlang Solutions wins business with BoardClic in a new era of collaboration
Erlang Solutions, a world-leading provider of software development and consultancy services, is pleased to announce its latest customer win with BoardClic, the leading platform for digital board performance reviews.
Following a successful Elixir code and architecture review, Erlang Solutions has been appointed to deliver advanced Elixir development for BoardCli … ⌘ Read more
What’s new with GitHub Copilot: July 2024
To enhance your coding experience, AI tools should excel at saving you time with repetitive, administrative tasks, while providing accurate solutions to assist developers. Today, we’re spotlighting three updates designed to increase efficiency and boost developer creativity.
The post What’s new with GitHub Copilot: July 2024 appeared first on [The GitHu … ⌘ Read more
Applying the DRY principle to Kyverno policies
Member post originally published on the Nirmata Blog by Jim Bugwadia The Don’t Repeat Yourself (DRY) principle of software development advocates avoiding repetition of code that is likely to change. Replacing similar code with reusable abstractions makes software easier to… ⌘ Read more
Beginner’s guide to GitHub: Adding code to your repository
Take the next step in our GitHub for Beginners series and add code to your repository. Learn how to create branches and upload changes into a pull request.
The post Beginner’s guide to GitHub: Adding code to your repository appeared first on The GitHub Blog. ⌘ Read more
@prologic@twtxt.net I don’t think it’s your code. As you said in one of your commit comments, the internet is a hostile place! That’s partly why I reacted the way I did: all things considered it’s usually better to react quickly and clean up the mess later, then it is to wait and risk further damage. Anyway it sucks @xuu@txt.sour.is got caught up in it. Hopefully it’s all good now.
How to review code effectively: A GitHub staff engineer’s philosophy
GitHub Staff Engineer Sarah Vessels discusses her philosophy of code review, what separates good code review from bad, her strategy for finding and reviewing code, and how to get the most from reviews of her own code.
The post [How to review code effectively: A GitHub staff engineer’s philosophy](https://github.blog/developer-skills/github/how-to-review-code-effectively-a-github-staff-eng … ⌘ Read more
3 ways to get Remote Code Execution in Kafka UI
In this blog post, we’ll explain how we discovered three critical vulnerabilities in Kafka UI and how they can be exploited.
The post 3 ways to get Remote Code Execution in Kafka UI appeared first on The GitHub Blog. ⌘ Read more
It took me so long to find the cause of a memory leak in GoBlog. I thought it was smart to use a cache for prepared database statements. But I didn’t read the documentation and didn’t know that prepared statements need to be closed when they are no longer needed to free up the allocated resources. 🤦♂️ I finally fixed it by removing the prepared statement cache altogether. Less code, fewer problems in the future, and the cache wasn’t much of an improvement anyway. I also learned about the usefulness of memory profil … ⌘ Read more
The XMPP Standards Foundation: The XMPP Newsletter June 2024
XMPP Newsletter Banner
Welcome to the XMPP Newsletter, great to have you here again!
This issue covers the month of June 2024.
The XSF has been accepted as a hosting organisation at GSoC in 2024 again!
These XMPP projects have received a slot and have kicked-off with … ⌘ Read more
After that talk about the Ladybird browser the other day, I see this article just pop up:
Seems it’s gaining some recognition and support, I hope it can gain traction as we sure as anything need some genuine alternatives.
Base: 4.25 miles, 00:09:47 average pace, 00:41:35 duration
carrying on from code brown
#running #treadmill
Base: 1.75 miles, 00:09:42 average pace, 00:16:58 duration
had to stop for code brown.
#running #treadmill
It seems like I finally fixed a memory leak in GoBlog yesterday, that sometimes made my blog crashing. How? I used Anthropic’s new Claude 3.5 Sonnet to write me a new HTTP compression middleware that compresses HTTP responses using zstd or gzip when possible. I needed to instruct a few changes and modify some code lines as the initial implementation was wrong, but thereafter, it finally seems to work better than my original implementation that probably leaked some objects anywhere. Claude also helped me to write uni … ⌘ Read more
ReadMeAI: An AI-powered README Generator for Developers
The ReadMeAI tool allows users to upload a code file and describe their project. The tool generates documentation in Markdown code for immediate preview and editing. ⌘ Read more
Attack of the clones: Getting RCE in Chrome’s renderer with duplicate object properties
In this post, I’ll exploit CVE-2024-3833, an object corruption bug in v8, the Javascript engine of Chrome, that allows remote code execution (RCE) in the renderer sandbox of Chrome by a single visit to a malicious site.
The post [Attack of the clones: Getting RCE in Chrome’s renderer with duplicate object properties](https://github.blog/2024-06-26-attack-of-the-cl … ⌘ Read more
Why you do not want a visualization of your Infrastructure as Code
Originally published on the appCD blog by Asif Awan You’ve been working on a new application for your company. It is going to address business requirements needed to delight customers. But while you are ready to ship your… ⌘ Read more
Execute commands by sending JSON? Learn how unsafe deserialization vulnerabilities work in Ruby projects
Can an attacker execute arbitrary commands on a remote server just by sending JSON? Yes, if the running code contains unsafe deserialization vulnerabilities. But how is that possible? In this blog post, we’ll describe how unsafe deserialization vulnerabilities work and how you can detect them in Ruby projects.
The post [Execute c … ⌘ Read more
@prologic@twtxt.net hey mate, all working well here so far. The login issue isn’t really an issue as far as actually logging in goes, rather if I get my password wrong it gives the response error code in console, the response of which contains the HTML for the wrong password page if you inspect it, but on the frontend itself nothing actually happens which is the confusion. Just stays on the login page as if it was never submitted. Am I alone in having this issue as well?
How we improved push processing on GitHub
Pushing code to GitHub is one of the most fundamental interactions that developers have with GitHub every day. Read how we have significantly improved the ability of our monolith to correctly and fully process pushes from our users.
The post How we improved push processing on GitHub appeared first on The GitHub Blog. ⌘ Read more
Tulip Creative Computer: ESP32-Based Board for Music and Coding Projects
The Tulip Creative Computer is a development platform aimed at enthusiasts of coding, music, and digital arts. Based on the powerful ESP32-S3 chipset, the Tulip features a 7-inch touchscreen with a 1024 x 600 resolution for custom graphical user interfaces. The Tulip Creative Computer is powered by the ESP32-S3 chip, which includes a 32-bit LX7 […] ⌘ Read more
New York Times Source Code Leaked (and verified)
Over 3.6 Million files totaling over 334 GB. And it’s real. Source code. Documentation. Markdown files. The works. ⌘ Read more
Build Your Own AI-Driven Code Analysis Chatbot for Developers with the GenAI Stack
We dive into a winning Docker AI/ML Hackathon submission, Code Explorer, in the hope that it sparks project ideas for you. ⌘ Read more
GitHub and JFrog partner to unify code and binaries for DevSecOps
This partnership between GitHub and JFrog enables developers to manage code and binaries more efficiently on two of the most widely used developer platforms in the world.
The post GitHub and JFrog partner to unify code and binaries for DevSecOps appeared first on The GitHub Blog. ⌘ Read more
Room Code
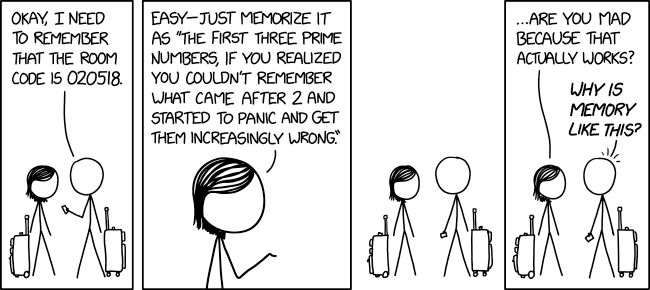 ⌘ Read more
⌘ Read more
Scaling accessibility within GitHub and beyond
GitHub celebrates Global Accessibility Awareness Day by launching another installment of the Coding Accessibility series and sharing how we scale accessibility within GitHub and beyond.
The post Scaling accessibility within GitHub and beyond appeared first on The GitHub Blog. ⌘ Read more
This blog has no Onion Service anymore
I had Tor support in GoBlog for over three years now, but I decided to disable it on my blog (and the GoBlog blog) for now. Several times, Tor randomly started using a lot of memory on my VPS and even crashed my block one or two times. It could have been the Go library used to integrate Tor, or something else in the Tor code itself, I don’t know. ⌘ Read more
How AI enhances static application security testing (SAST)
Here’s how SAST tools combine generative AI with code scanning to help you deliver features faster and keep vulnerabilities out of code.
The post How AI enhances static application security testing (SAST) appeared first on The GitHub Blog. ⌘ Read more
GitHub Copilot Chat in GitHub Mobile is now generally available
With GitHub Copilot Chat in GitHub Mobile, developers can collaborate, ask coding questions, and gain insights into both public and private repositories anywhere, anytime–all in natural language for users on all GitHub Copilot plans.
The post GitHub Copilot Chat in GitHub Mobile is now generally available appeared first on The GitHub Blog. ⌘ Read more
Is your supply chain secure? Double check with our framework
A secure supply chain is a critical piece of cloud native security, and it can be tricky to get right because it covers such a broad expanse of factors from code to pipelines and beyond. Join us on… ⌘ Read more
5 tips to supercharge your developer career in 2024
From mastering prompt engineering to leveraging AI for code security, here’s how you can excel in today’s competitive job market.
The post 5 tips to supercharge your developer career in 2024 appeared first on The GitHub Blog. ⌘ Read more
GitHub Copilot Workspace: Welcome to the Copilot-native developer environment
We’re redefining the developer environment with GitHub Copilot Workspace - where any developer can go from idea, to code, to software all in natural language.
The post GitHub Copilot Workspace: Welcome to the Copilot-native developer environment appeared first on The GitHub Blog. ⌘ Read more
Microsoft Releases DOS 4.0 Source Code… but it Doesn’t Compile!
Listen now (56 mins) | Plus: Source comments, by Microsoft, calling the creator of DOS “brain-damaged” get censored. ⌘ Read more
MS-DOS 4.0 Source Code Fails to Compile
Plus: Source comments, by Microsoft, calling the creator of DOS “brain-damaged” get censored. ⌘ Read more
Erlang Solutions: Technical debt and HR – what do they have in common?
At first glance, it may sound absurd. Here we have technical debt, a purely engineering problem, as technical as it can get, and another area, HR, dealing with psychology and emotions, put into one sentence. Is it possible that they are closely related? Let’s take it apart and see.
What is technical debt, anyway? A tongue-in-cheek definition is that it is code written by someo … ⌘ Read more
What is infrastructure from code?
Member post originally published on AppCD’s blog by Lauren Rother Maybe you’ve heard of Infrastructure as Code (IaC), which is the process of managing and provisioning computer data center resources (mostly but not entirely in the cloud) through version-controlled, machine-readable… ⌘ Read more
Even though the bridges that #beeper use are AGPL licensed, the beeper client is proprietary software 😭
This is big sad.
They almost had it.
It is also kind of limited on google-free android phones, since the QR code scanner for device verification key-signing depends on a google play services API (which microg doesn’t implement). This means that you can’t share message history between your google-free android and the beeper desktop client. ⌘ Read more
Added support for #tag clouds and #search to timeline. Based on code from @dfaria.eu@dfaria.eu🙏
Live at: http://darch.dk/timeline/?profile=https://darch.dk/twtxt.txt
Membership change source code interpretation
Member post originally published on Medium by DatenLord Background In distributed system application scenarios, it is inevitable to add or delete nodes or replace nodes, the simplest solution is to temporarily shut down the cluster, then directly modify… ⌘ Read more
Security research without ever leaving GitHub: From code scanning to CVE via Codespaces and private vulnerability reporting
This blog post is an in-depth walkthrough on how we perform security research leveraging GitHub features, including code scanning, CodeQL, and Codespaces.
The post [Security research without ever leaving GitHub: From code scanning to CVE via Codespaces and private vulnerability reporting](htt … ⌘ Read more
OpenSSH and XZ/liblzma: A nation-state attack was thwarted, what did we learn?
Docker CTO Justin Cormack looks at what we can learn from malicious code in upstream tarballs of xz targeted at subset of OpenSSH servers. “It is hard to overstate how lucky we were here, as there are no tools that will detect this vulnerability.” ⌘ Read more