A Complete Guide to Securing Secrets in AWS Lambda
Learn how to securely manage secrets in AWS Lambda using environment variables, KMS encryption, Secrets Manager, and more.
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/a-c … ⌘ Read more
Should Taxpayer Money Fund Open Source?
Mozilla, F-Droid, Let’s Encrypt, Tor, & more receive huge amounts of money from US taxes. ⌘ Read more
Tor, F-Droid, & Let’s Encrypt Lose Tax Payer Funding, Go To Court
The US tax payer funded Open Technology Fund has lost Federal funding and is taking the Trump administration to court. ⌘ Read more
Istio: The Highest-Performance Solution for Network Security
Ambient mode provides more encrypted throughput than any other project in the Kubernetes ecosystem. Encryption in transit is a baseline requirement for almost all Kubernetes environments today, and forms the foundation of a zero-trust security posture…. ⌘ Read more
France rejects backdoor mandate
Article URL: https://www.eff.org/deeplinks/2025/03/win-encryption-france-rejects-backdoor-mandate
Comments URL: https://news.ycombinator.com/item?id=43440513
Points: 500
# Comments: 124 ⌘ Read more
Erlang Solutions: Top 5 IoT Business Security Basics
IoT is now a fundamental part of modern business. With more than 17 billion connected devices worldwide, IoT business security is more important than ever. A single breach can expose sensitive data, disrupt operations, and damage a company’s reputation.
To help safeguard your business, we’ll cover five essential IoT security basics: data encryption, strong password policies, regular security audits, employee awareness tr … ⌘ Read more
ameriDroid Opens Preorders for VPN Server with WireGuard and DietPi
The VPN Server by ameriDroid is a pre-configured device for secure remote access to home and small office networks. Built on the ODROID-C4, it runs a lightweight Linux-based system with WireGuard for encrypted VPN connections and minimal setup. The device is based on the ODROID-C4, a single-board computer released in early 2020 by Hardkernel, featuring […] ⌘ Read more
Let’s Encrypt ends support for expiration notification emails
Since its inception, Let’s Encrypt has been sending expiration notification emails to subscribers that have provided an email address to us. We will be ending this service on June 4, 2025. ↫ Josh Aas on the Let’s Encrypt website They’re ending the expiration notification service because it’s costly, adds a ton of complexity to their systems, and constitutes a privacy risk because of all the email addresses the … ⌘ Read more
It’s ok for most encrypted protocols (In salty you can fetch other messages but can’t decrypt). Btw i think recipient can be removed so if someone seen message they tried to decypt, if can’t - its not message to you
Apple has agreed to pay $95 million to settle a lawsuit alleging that its voice assistant Siri routinely recorded private conversations that were then sold to third parties for targeted ads.
From Siri “unintentionally” recorded private convos; Apple agrees to pay $95M https://arstechnica.com/tech-policy/2025/01/apple-agrees-to-pay-95m-delete-private-conversations-siri-recorded/
I’m not sure I’m convinced Apple is really that much better than the other big tech companies when it comes to this kind of thing. Their reputation is better and they do seem to be better about things like on-device encryption, but then stories like this come out.
[WTS] [$1.5K USD] Encrypted Graphene OS Pixels Fully Setup
PIXEL 6, 6a, 6 Pro, 7a, 7, 7 Pro, 8a, 8 Pro
Link: https://moneromarket.io/listing/e6cd0a03-238b-434f-9a25-382e8da30725
u/Encrypto84 (MoneroMarket.io) ⌘ Read more
Cloud Native Computing Foundation Announces cert-manager Graduation
Open source security project automates highly secure, encrypted data communications in cloud native environments SALT LAKE CITY, Utah – KubeCon + CloudNativeCon North America – November 12, 2024 – The Cloud Native Computing Foundation® (CNCF®), which… ⌘ Read more
Oof, is it any wonder some of us don’t want to just give out our info online willy-nilly.
Also that credit card ‘encryption’ will likely land that company in very hot water, no doubt far away from PCI DSS requirements.
Lol. “Lighty Encrypted” https://www.pcmag.com/news/hot-topic-breach-confirmed-millions-of-credit-cards-email-addresses-exposed
Malleable Encryption - Computerphile ⌘ Read more
Malleable Encryption - Computerphile ⌘ Read more
Encryption matters
Community post by Ronald Petty and Tom Thorley of the Internet Society US San Francisco Bay Area Chapter (original post) When you hear the word encryption, what comes to mind? Take a moment… Upon asking this question to… ⌘ Read more
@prologic@twtxt.net a signature IS encryption in reverse. If my private key becomes compromised then they can impersonate me. Being able to manage promotion and revocation of keys needed even in a system where its used for just signatures.
Gajim: Gajim 1.9.2
Gajim 1.9.2 brings an important OMEMO encryption fix, native notifications on Windows, usability improvements, and many bugfixes. Thank you for all your contributions!
For some versions now, Windows offers a native notification system, including a notification center for unread notifications, notification settings, etc. If you are running Windows 10 (specifically build 10240) or later versions, Gajim will now use these native notifications.
Thanks to our contributor [@nico … ⌘ Read more
Automattic are also a company that has sold user data from tumblr and wordpress.com to openai and midjourney, so you might want to keep that in mind if you’re big against generative AI.
Beeper servers store the message history encrypted, with a key that isn’t sent to the server.
Everything they store is encrypted with these keys, *but* I guess they still can’t encrypt the messages in transit because of the interop dance; so they *can* read messages to some networks at some point. ⌘ Read more
AES GCM (Advanced Encryption Standard in Galois Counter Mode) - Computerphile ⌘ Read more
@shreyan@twtxt.net What do you mean when you say federation protocol?
Either use webfinger for identity like mastodon etc. or use ATproto from Bluesky (or both?)
We can use webmentions or create our own twt-mentions for notifying someones feed (WIP code at: https://github.com/sorenpeter/timeline/tree/webmention/views)
I’m not sure we need much else. I would not even bother with encryption since other platforms does that better, and for me twtxt/yarn/timeline is for making things public
how would that work with your encryption keys? you send them to a server that hopefully you control?
@lyse@lyse.isobeef.org I have read the white papers for MLS before. I have put a lot of thought on how to do it with salty/ratchet. Its a very good tech for ensuring multiple devices can be joined to an encrypted chat. But it is bloody complicated to implement.
Ignite Realtime Blog: Certificate Manager plugin for Openfire release 1.1.1
The Ignite Realtime community is happy to announce a new release of the Certificate Manager plugin for Openfire.
This plugin allows you to automate TLS certificate management tasks. This is particularly helpful when your certificates are short-lived, like the ones issued by Let’s Encrypt.
This release is a maintenance release. It adds translations. More details are available in the [changelog] … ⌘ Read more
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
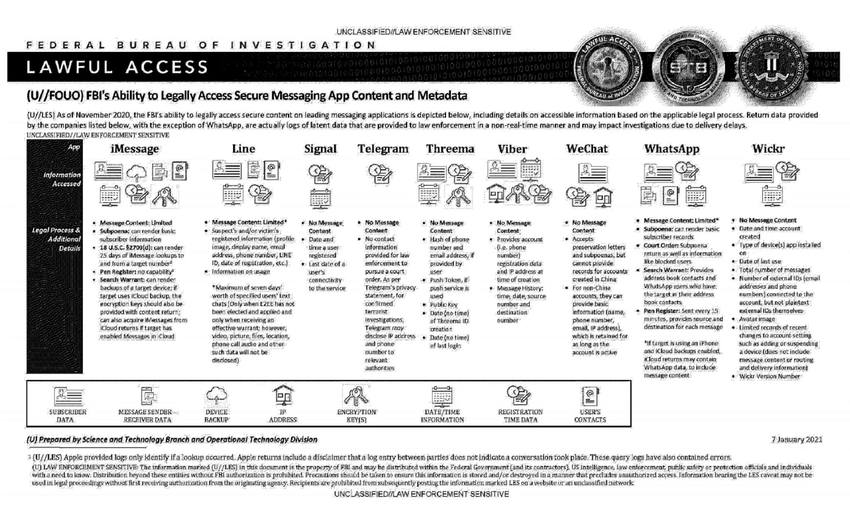
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
I setup Joplin with caddy as the WebDAV server. Works okay. The e2e encryption can get messed up sometimes. Supports markdown and images.
Gajim: Gajim 1.8.0
Gajim 1.8.0 comes with integrated OMEMO encryption! Integrating the OMEMO plugin brings tighter integration and better user experience. We also rearranged the chat menu and added some quick buttons for convenience. Both Gajim’s message search and conversation view received some important changes and fixes. Thank you for all your contributions!
In the past, we moved the most popular plugins into Gajim’s core: image preview, plugin installer, HTTP file upload, syntax highligh … ⌘ Read more
Kaidan: Kaidan 0.9: End-to-End Encryption & XMPP Providers
It’s finally there: Kaidan with end-to-end encryption via OMEMO 2, Automatic Trust Management and support of XMPP Providers!
Most of the work has been funded by NLnet via NGI Zero PET and NGI Assure with [public … ⌘ Read more
**RT by @mind_booster: 1/3 🚨Recent @POLITICOEurope leak revealed that US & EU officials have agreed to cooperate on measures to turn public opinion against #encryption.
Experts’ statements by @edri & @globalencrypt have called out against this plan
➡️https://edri.org/our-work/eu-us-plan-offensive-to-legitimise-police-access-to-data-civil-society-responds-amid-growing-fears-press-release/
➡️https://www.globalencryption.org/2023/04/statement-on-eu-us-cooperation-against-encryption/**
1/3 🚨Recent [@POLITICOEurope](https … ⌘ Read more
https://simplex.chat/ First messenger without user IDs with end to end encryption
My cheap alternative to Ngrok
Since GoBlog has an Auto-HTTPS feature that can automatically retrieve HTTPS certificates via ACME from e.g. Let’s Encrypt, I need a public IP address with which I can reach my test instance of GoBlog via port 80 and 443. ⌘ Read more
JMP: SMS Account Verification
Some apps and services (but not JMP!) require an SMS verification code in order to create a new account. (Note that this is different from using SMS for authentication; which is a bad idea since SMS can be easily intercepted, are not encrypted in transit, and are v … ⌘ Read more
https://github.com/MihanEntalpo/cryptboard.io web clipboard and simple messanger with end-to-end encryption
Jérôme Poisson: Libervia progress note 2022-W45
Hello, it’s time for a long overdue progress note.
I’ll talk here about the work made on ActivityPub (AP) gateway and on end-to-end encryption around pubsub.
Oh, and if everything goes well, this blog post should be accessible from XMPP and ActivityPub (and HTTP and ATOM feed), using the same identifier goffi@goffi.org.
The work made on the AP gateway has been possible thanks to a NLnet/NGI0 grant (w … ⌘ Read more
Encryption & Entropy - Computerphile ⌘ Read more
How GitHub converts previously encrypted and unencrypted columns to ActiveRecord encrypted columns
This post is the second part in a series about ActiveRecord::Encryption that shows how GitHub upgrades previously encrypted and unencrypted columns to ActiveRecord::Encryption. ⌘ Read more
PSA: DMs on social media sites are not truely PMs. This is why we have a separate tool for private messaging from yarn. Always remember, if you don’t own the infra (or the parts at the ends of e2e encryption) you don’t own the data. and the true owners can view it any way they want!
https://twitter.com/TinkerSec/status/1587040089057759235?t=At-8r9yJPiG6xF17skTxwA&s=19
JMP: SMS Account Verification
Some apps and services (but not JMP!) require an SMS verification code in order to create a new account. (Note that this is different from using SMS for authentication; which is a bad idea since SMS can be easily intercepted, are not encrypted in transit, and are v … ⌘ Read more
Encryption
 ⌘ Read more
⌘ Read more
https://libreboot.org/docs/gnulinux/guix.html llvm encrypted
Why and how GitHub encrypts sensitive database columns using ActiveRecord::Encryption
You may know that GitHub encrypts your source code at rest, but you may not have known that we encrypt sensitive database columns as well. Read about our column encryption strategy and our decision to adopt the Rails column encryption standard. ⌘ Read more
JMP: SMS Account Verification
Some apps and services (but not JMP!) require an SMS verification code in order to create a new account. (Note that this is different from using SMS for authentication; which is a bad idea since SMS can be easily intercepted, are not encrypted in transit, and are v … ⌘ Read more
Paul Schaub: Using Pushdown Automata to verify Packet Sequences
As a software developer, most of my work day is spent working practically by coding and hacking away. Recently though I stumbled across an interesting problem which required another, more theoretical approach;
An OpenPGP message contains of a sequence of packets. There are signatures, encrypted data packets and their accompanying encrypted session keys, compressed data and literal data, the latter being the packet … ⌘ Read more
Kaidan: Encrypted Audio and Video Calls
Kaidan will receive a grant by NLnet for adding encrypted audio and video calls.
The calls will be end-to-end encrypted and authenticated via OMEMO.
Furthermore, Kaidan will support small group calls.
We strive for interoperability between Kaidan and other XMPP apps supporting calls.
In order to achie … ⌘ Read more
Kaidan: Kaidan’s End-to-End Encryption Trust Management
We worked several months on Kaidan’s upcoming end-to-end encryption and trust management.
Once Kaidan 0.9 is released, it will provide the latest OMEMO Encryption.
But it will also make trust decisions in the background for you if it’s possible.
Some trust decisions have to be made manually but there are many others Kaidan automates without decreasing your security.
That is done by automatically sharing … ⌘ Read more
I maintain keys for my email addresses.. but like most in this thread i almost never receive encrypted emails.. other than the BTC exchange i use that sends automated mail encrypted.
SourceHut encrypts all emails if PGP key is uploaded to user profile (can be disabled in settings). Just… wow!
**RT by @mind_booster: ½ 📢The Commission wants to do the impossible of detecting illegal content in end-to-end encrypted communications, but has no idea how to do this (because it IS impossible).
Solution: leave it to service providers under the guise of technological neutrality.**
½ 📢The Commission wants to do the impossible of detecting illegal content in end-to-end encrypted communications, but has no idea how to do this (because it IS impossible).
Solution: leave it to service providers under the guise of te … ⌘ Read more
When you submit a GDPR request to American Express (Germany), you get an “Encrypted Mail” (for which you have to log in again somewhere and set a password), which then contains two PDFs, one of which is full of screenshots of mainframe terminals. ⌘ Read more