Sometimes things happen that you did not expect: You hear a song, you really like it, you research who made it, and you find out that person lives in the same town as you: AK – Discovery. ⌘ Read more
@prologic@twtxt.net I know! I know! 🤣 and it feels like I won’t be either, at least for a while … On the bright #Go side, I’m trying to switch everything (static web stuff and reverse-proxy) to #Caddy
[ANN] MAGIC Monero Fund 2025 Election Results
ack-j and kowalabearhugs will serve 2-year terms. rottenwheel, Tacolopo, and XMRfamily will serve 1-year terms. Their terms will begin on January 31, 2025. We would like to thank all six committee candidates! We would like to thank everyone who voted!
Committee Members:
* ack-j
* kowalabearhugs
* rottenwheel
* Tacolopo
* XMRfamily
Link: [https://magicgrants.org/2025/01/21/Monero-Fund-2025-Election-Results.html](https://magicgrants.org/2025/01/21/Monero-Fund-2025 … ⌘ Read more
Right to root access
I believe consumers, as a right, should be able to install software of their choosing to any computing device that is owned outright. This should apply regardless of the computer’s form factor. In addition to traditional computing devices like PCs and laptops, this right should apply to devices like mobile phones, “smart home” appliances, and even industrial equipment like tractors. In 2025, we’re ultra-connected via a network of devices we do not have full control over. Much of this has t … ⌘ Read more
How UNIX spell ran in 64kB RAM
How do you fit a 250kB dictionary in 64kB of RAM and still perform fast lookups? For reference, even with modern compression techniques like gzip -9, you can’t compress this file below 85kB. In the 1970s, Douglas McIlroy faced this exact challenge while implementing the spell checker for Unix at AT&T. The constraints of the PDP-11 computer meant the entire dictionary needed to fit in just 64kB of RAM. A seemingly impossible task. ↫ Abhinav Upadhyay They still managed to … ⌘ Read more
Linux Distro Declared “Non-Woke”, Causing New Users & Interest to Skyrocket
While “Woke” Linux Distributions (like openSUSE) are struggling to survive, interest in OpenMandriva - a non-Woke Open Source project - is exploding. ⌘ Read more
Linux 6.13 released
Linux 6.13 comes with the introduction of the AMD 3D V-Cache Optimizer driver for benefiting multi-CCD Ryzen X3D processors, the new AMD EPYC 9005 “Turin” server processors will now default to AMD P-State rather than ACPI CPUFreq for better power efficiency, the start of Intel Xe3 graphics bring-up, support for many older (pre-M1) Apple devices like numerous iPads and iPhones, NVMe 2.1 specification support, and AutoFDO and Propeller optimization support when compiling the Linux kernel with … ⌘ Read more
Why don’t Australians source more coffee from our region?
Australia is surrounded by coffee-growing countries like Papua New Guinea and Indonesia, but it imports most of its coffee from the other side of the world. With climate change and coffee bean prices skyrocketing, is it time to look closer to home? ⌘ Read more
Flat white price likely to skyrocket this year, no matter where you live
Industry insiders say coffee lovers — even in regional Australia — are unlikely to escape paying more for their flat whites as cafes are forced to push up prices. ⌘ Read more
HackCable: USB-C Keystroke Injection Cable with RP2040 or ESP32
Kickstarter recently featured the HackCable, a USB-C cable designed for cybersecurity research and system testing. It resembles a standard charging cable but includes features like built-in Wi-Fi and keystroke injection, providing a discreet and versatile tool for professionals and researchers. HackCable is available in two versions, each powered by a different microcontroller: the ESP32-S3 or […] ⌘ Read more
MorphOS 3.19 released
It’s been about 18 months, but we’ve got a new release for MorphOS, the Amiga-like operating system for PowerPC Macs and some other PowerPC-based machines. Going through the list of changes, it seems MorphOS 3.19 focuses heavily on fixing bugs and addressing issues, rather than major new features or earth-shattering changes. Of note are several small but important updates, like updated versions of OpenSSL and OpenSSH, as well as a ton of new filetype definitions – and so much more. Havin … ⌘ Read more
@movq@www.uninformativ.de my friend, I’m curious what is that interface? It’s like WindowMaker meets dwm, meets…? :D
Sounds like a plan
creating a twtxt timeline page for tilde.club.. will see if anyone likes it when its done
creating a twtxt timeline page for tilde.club.. will see if anyone likes it when its done
damn it i got so excited because bleeding cool ran an article with a title like ‘all of DC april solicits so far’ and i did not read the ‘so far’ part and clicked it excitedly hoping to see all the april solicits but they’re out next week or something T__T
@lyse@lyse.isobeef.org OMGGGG I’M BRINGING AKB TO YARN LET’S GOOOOO!!!! SO glad you like them they make bangers!!!!! super catchy and fun <333
@lyse@lyse.isobeef.org i’m a horrible gamer but i do best when playing kart racing games like this and mario kart haha!
Human Altitude
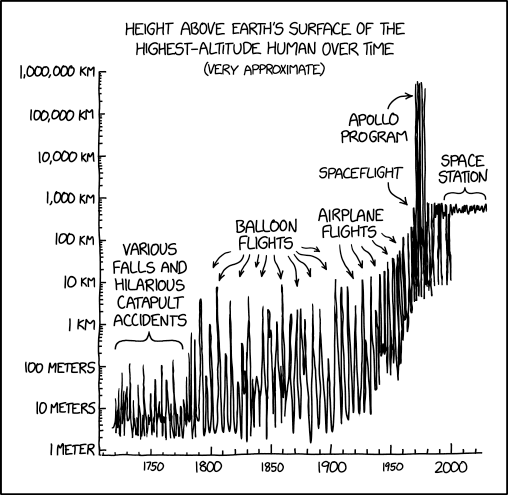 ⌘ Read more
⌘ Read more
@prologic@twtxt.net they post pretty frequently yeah, new articles like every other day basically
** Oh so many peas **
I accidentally spilled close to a full bag of frozen peas into the pot while making macaroni and cheese for the kids’ dinner this evening.
It was like 2 to 1 peas in there…and they ate it up. Didn’t seem to mind at all!? ⌘ Read more
** Sirens & Muses **
I finished reading Sirens & Muses by Antonia Angress.
It left me gutted, but like in a good way. It leaves so much unsaid, which I found pleasant and sorrowful and so yawningly, humongously open that it left me feeling a little claustrophobic.
A few years ago everyone, everyone, everyone I spoke to about books told me again and again and again to read Gabrielle Zevin’s Tomorrow, and Tomorrow, and Tomorrow. I found it to be totally and completely lacking in joy and any sort of human warmth, and, I think th … ⌘ Read more
Platform engineering at KubeCon + CloudNative NA 2024 in Salt Lake City
Ambassador post originally published on Medium by Mathieu Benoit, CNCF Ambassador KubeCon NA 2024 in Salt Lake City was a blast! Like always, I met with old friends, I made new friends and I had deep… ⌘ Read more
i self hosted the soft serve git server cuz i felt like it. it’s sooo cute i love everything charm CLI does
ssh -p 24010 soft.git.girlonthemoon.xyz
Wussup twtxt I’m rolling cigarettes (I don’t smoke) (I think it’s funny) (it’s like crocheting a scarf when you don’t wear scarves)
Voice Preview Edition: Open-Source Design with Local Processing Capabilities
The Home Assistant Voice Preview Edition is an open-source voice assistant designed for integration with Home Assistant systems. It emphasizes privacy, local processing, and compatibility with smart home hardware, offering reliable performance and flexible usability. The device features dual microphones and an XMOS XU316 audio processor for advanced capabilities like echo cancellation, noise … ⌘ Read more
@doesnmppsflt@doesnm.p.psf.lt It looks like it… Although they shouldn’t be empty since Timeline took care of sending those. I believe I have an idea as to why that happened, but will have to test before filing an issue.
** Styrofoam cups and awk **
I like writing these posts for my website, but I’ve sat down to write this one like 11 times and it either takes on a tone of totally encompassing dread and dystopian navel gazing or I feel like I’m burying my head in the sand and ignoring reality as it happens around me.
…I finished reading Victor LaValle’s The Changeling. It was engaging, and I was interested in where it was going, but I found that where it went wasn’t interesting. The dialogue and prose were lively and contemporary, which is what r … ⌘ Read more
Checked my posthook… looks like my bash skills at zero: https://doesnm.cc/huh.txt
Pinellas County - Long Run: 8.50 miles, 00:09:50 average pace, 01:23:31 duration
garmin gps really fucked this one up. it thought i ran a half marathon at like a 7:00 pace or something.
the run was okay. it was a bit warmer and humid this morning, but really i am just a bit worn out i think. it was a bit boring so i turned on the podcast “telepathy tapes” and that was at least background noise.
#running
10 Things You May Not Know About the London Underground
The London Underground, affectionately known as “The Tube,” is much more than a transit system. It’s an iconic symbol of London and a marvel of engineering history, weaving through the city and its surrounding counties like veins of a bustling metropolis. First introduced as the Metropolitan Railway in 1863, the Underground was the world’s first […]
The post [10 Things You May Not Know About the London Underground](https:/ … ⌘ Read more
[LTH] Looking for someone to turn a picture of a face into half cyborg, like terminator
Link: https://farside.link/libreddit/r/HireAiArtist/comments/1hz1ajt/
u/iron_armored (Reddit) ⌘ Read more
nick is yo? Btw say me which method you choiced. I want to make mention fixer like @bender -> @bender@twtxt.net in my post-hook
Use “Type to Siri” on Mac Easier Than Ever in Sequoia
Siri has been considerably improved in recent MacOS versions, mostly because it’s now linked to ChatGPT. One of the other recent changes to Siri in modern MacOS versions is that it’s now easier to access the “Type to Siri” feature, no longer being relegated to an Accessibility setting that has to be enabled separately like … Read More ⌘ Read more
@kat@yarn.girlonthemoon.xyz i don’t even have like time or space to stream unless it was no mic/video and just me doing stuff on my computer which can be boring without even mic input. plus no way to use camcorder that way. but. it’d be cool if i could so i dream
@prologic@twtxt.net i thought i was going insane when i saw blank posts on my TL i was like is noscript fucking with me again but no it’s you guys fucking around LOLLLL
Hello @movq@uninformativ.de . Did you fixed jenny bug which causes fetching long ids from yarn instances on feeds like https://ciberlandia.pt/@marado.txt ? I’m asking because i want to store links in brackets on some of my posts and don’t want to confuse jenny users
Show HN: Tetris in a PDF
I realized that the PDF engines of modern desktop browsers (PDFium and PDF.js) support JavaScript with enough I/O primitives to make a basic game like Tetris.
It was a bit tricky to find a union of features that work in both engines, but in the end it turns out that showing/hiding annotation “fields” works well to make monochrome pixels, and keyboard input can be achieved by typing in a text input box.
All in all it’s quite janky but a nice reminder of how general purpose PDF scripting can be. The lin … ⌘ Read more
wrote up a short list of things i need to do for superlove… it’s just some like clarification and housekeeping and stuff really
@prologic@twtxt.net it’s pretty new for me but i’m liking it so far!
taskbook is really neat. i like using its to-do features, i think the note-taking i won’t need as i’ve been using obsidian a lot for that lately but the to-do stuff is really helping me out
edited the theming on my zine posts on itch.io, i like how they look!
Show HN: Tramway SDK – An unholy union between Half-Life and Morrowind engines
Hello everyone, I would like to see if there is any interest in this little project that I have been working on for the past few years.
Could be relevant, seeing the direction in which the mainstream game engines are going.
I didn’t really like any of the already existing options, so I tried to make my own and it turned out to be easier than expected.
It’s sort of like a low-budget Unreal/Source, but with open-world streaming support and it is … ⌘ Read more
I keep forgetting how much socialization with people I actually like really helps ease up my depression for a bit.
@prologic@twtxt.net awww thank you! yeah i’d love to keep it small and chill. that’s what i and my friends like most about yarn, how small and quiet it is, it’s just chill! and there’s no likes/reposts too which helps keep it super chill i think. just vibes… it’s the best! you’ve built something great!
@prologic@twtxt.net would it be enough to spin up a reverse proxy/Tunnel like the one you did? 😏
@bender@twtxt.net oh yeah i remember that part of the docs lol! honestly yeah i think sqlite is fine for the number of users i have which is like, 5 including me, and active users is just… me, but if i were to have more active users i could always spin up a separate instance as jank as that is
@kat@yarn.girlonthemoon.xyz i’m an LXQt girlie for life and i like the convenience of apt despite that they never update their god damn packages so i guess i’m stuck on lubuntu for everything
hmmm i really should set up crowdsec and maybe a WAF like coraza or something. i don’t look at my logs as much as i should because they scare me and ignorance is bliss but i should probably cut out as much false traffic as possible especially to my biggest site (superlove)
10 Disturbing Superstitions That Killed
Humanity has always had a thing for superstitions—those quirky, often nonsensical beliefs that spice up our lives with a touch of paranoia. They have us knocking on wood when we tempt fate, giving black cats the side-eye, and detouring around ladders like they’re crime scenes. Harmless, right? Not always. While most superstitions are charming little […]
The post [10 Disturbing Superstitions That Killed](https://listverse.com/2025/01/06/10-disturbing-supe … ⌘ Read more