@lyse@lyse.isobeef.org I had that as my avatar/userprofile pic at work for a few years. 😆
@lyse@lyse.isobeef.org Luckily, yeah. Happens every now and then. It’s usually not even worth reporting, they often fix it in 30-90 minutes anyway.
@eapl.me@eapl.me this “directory” is actually named registry. You can see users at https://registry.twtxt.org/api/plain/users and his twts at https://registry.twtxt.org/api/plain/tweets
Hmm so looking at the swagger of the registry spec client it seems to just take a “page”.. That seems worse than doing an offset. Lol.
https://github.com/DracoBlue/twtxt-registry/blob/master/src/swagger.json
@bender@twtxt.net thinked about Gemini protocol. Why corporations shit this name with cryptocurrency and LLMs?
@xuu@txt.sour.is like feeds+bridgy.fed? Will be happy anyway
@doesnm@doesnm.p.psf.lt haha its not coming back. he talked of a stand alone thing like feeds. but not in yarnd
hmm @prologic@twtxt.net how did replying to lyse double up here?
about:compat in Firefox.
@lyse@lyse.isobeef.org I remember WebKit having a similar list, but I can’t find it right now … 🙈
@prologic@twtxt.net In all seriousness: Don’t worry, I’m not going to host some Fediverse thingy at the moment, probably never will. 😅
But I do use it quite a lot. Although, I don’t really use it as a social network (as in: following people). I follow some tags like #retrocomputing, which fills my timeline with interesting content. If there was a traditional web forum or mailing list or even a usenet group that covered this topic, I’d use that instead. But that’s all (mostly) dead by now. ☹️
@bender@twtxt.net That … was better than expected. 😂
The Mastodon admins say that it’s probably because of the size of my account (~600 MB), so the export process times out. And I understand that. Here on twtxt, I always use auto-expiring links when I post images or videos. It just gets too much data otherwise. I think I’ll just set my Mastodon account to auto-delete posts after ~180 days or something like that. Nobody cares about old posts anyway.
@lyse@lyse.isobeef.org @bender@twtxt.net It already is a tiling window manager, but some windows can’t be tiled in a meaningful way. I admit that I’m mostly thinking about QEMU or Wine here: They run at a fixed size and can’t be tiled, but I still want to put them in “full screen” mode (i.e., hide anything else).
@movq@www.uninformativ.de let’s host yarnd! Or maybe wait until @prologic@twtxt.net return activitypub support which deleted in this commit
@kat@yarn.girlonthemoon.xyz I have just opened the GIMP bug tracker (hosted at gitlab.gnome.org) and, I kid you not, they have deployed Anubis in front of it:
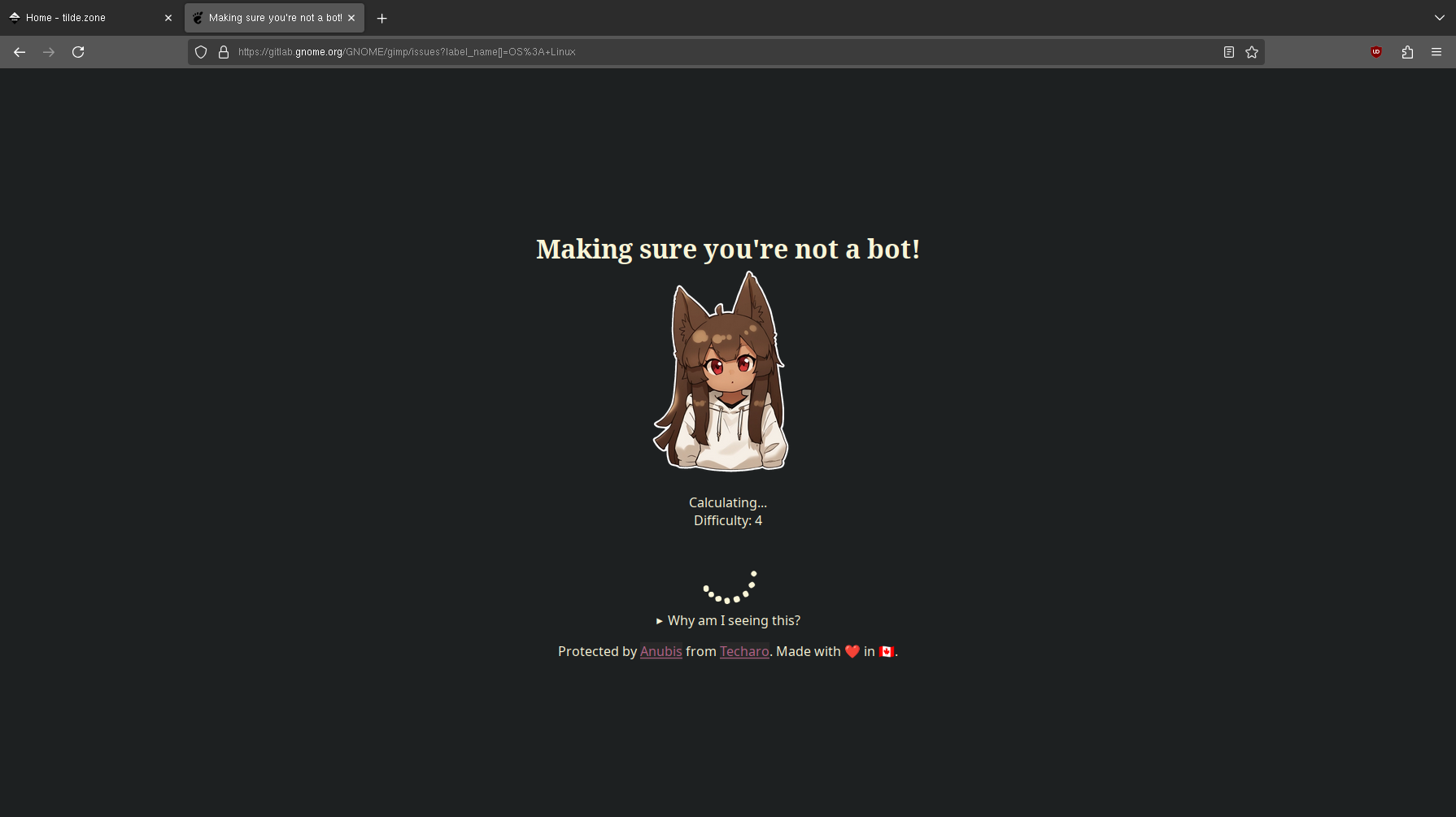
Oof.
@lyse@lyse.isobeef.org I’m glad to hear that! Yay for more clients. 😊
👋 Hello @mullerenergyco@we.loveprivacy.club, welcome to We.Love.Privacy.Club, a Yarn.social Pod! To get started you may want to check out the pod’s Discover feed to find users to follow and interact with. To follow new users, use the ⨁ Follow button on their profile page or use the Follow form and enter a Twtxt URL. You may also find other feeds of interest via Feeds. Welcome! 🤗
👋 Hello @mullerenergyco@we.loveprivacy.club, welcome to We.Love.Privacy.Club, a Yarn.social Pod! To get started you may want to check out the pod’s Discover feed to find users to follow and interact with. To follow new users, use the ⨁ Follow button on their profile page or use the Follow form and enter a Twtxt URL. You may also find other feeds of interest via Feeds. Welcome! 🤗
@lyse@lyse.isobeef.org Interesting, thanks for that list. 🤔
… yeah, okay, I don’t think I’ll do that. 😅 Anything but twtxt is just too much effort.
👋 Hello @robertskict@we.loveprivacy.club, welcome to We.Love.Privacy.Club, a Yarn.social Pod! To get started you may want to check out the pod’s Discover feed to find users to follow and interact with. To follow new users, use the ⨁ Follow button on their profile page or use the Follow form and enter a Twtxt URL. You may also find other feeds of interest via Feeds. Welcome! 🤗
👋 Hello @robertskict@we.loveprivacy.club, welcome to We.Love.Privacy.Club, a Yarn.social Pod! To get started you may want to check out the pod’s Discover feed to find users to follow and interact with. To follow new users, use the ⨁ Follow button on their profile page or use the Follow form and enter a Twtxt URL. You may also find other feeds of interest via Feeds. Welcome! 🤗
Although, most software I use is decentish in that regard.
Is that because you mostly use Qt programs? 🤔
I wish Qt had a C API. Programming in C++ is pain. 😢
@lyse@lyse.isobeef.org (I think of pointers as “memory location + type”, but I have done so much C and Assembler by now that the whole thing feels almost trivial to me. And I would have trouble explaining these concepts, I guess. 😅 Maybe I’ll cover this topic with our new Azubis/trainees some day …)
@lyse@lyse.isobeef.org Maybe it’s a lyrebird. 😏
@prologic@twtxt.net Yes, it was one of those. 95, 98, and Me were all built on top of DOS, as far as I know.
@lyse@lyse.isobeef.org I guess the thing is that usernames are no longer needed for many popular things, like WhatsApp. “Just install the app”, done. When I ran my Matrix server for our family, this was the first thing that people were bummed out about: “Oh, this needs a username and a password? Why doesn’t it just work? That’s annoying.”
People are less and less exposed to “low-level” details like this. There was also this story in 2021 about the concept of a “file”: https://www.theverge.com/22684730/students-file-folder-directory-structure-education-gen-z
@prologic@twtxt.net Yeah and I don’t get why … There’s no copyrighted music in it, no ads (at least I don’t see any) … Just weird. 🥴
@prologic@twtxt.net Lol, I give up. 🥴
@lyse@lyse.isobeef.org There’s a reason it’s called “(n)curses”. 😏 The only advice I can give is to never fiddle with reassigning control sequences and $TERM variables. Leave $TERM at whatever value the terminal itself sets and use an appropriate terminfo file for it. If there are programs misbehaving, they probably blindly assume XTerm and should be fixed (or have XTerm as a hard requirement). If you try to fix this on your end, it’ll likely just break other programs. 🥴
@david@collantes.us Ah, I just went to bed, great to see you figured it out. 😅 I probably would have ended up with something similar (but I’m not a Vimscript guru). 🤔
Chapter 14:
Epilogue:
Chapter 12:
Chapter 13:
@david@collantes.us While you’re typing? I guess this could be used as a starting point (doesn’t work on the very first line):
inoremap <CR> <Esc>:r!date +"\%F \%T"<CR>A
What’s the end goal here? 😅
@movq@www.uninformativ.de hahahah i for one hate sleeping and need to be busy 24/7 or else i go insane so server stuff is awesome for my ADHD ass!!!
IaaS does seem kinda interesting to me, i think i could vibe with that more than full on cloud stuff
i hope i can be one of those people who does the barebones stuff bc i am a rare sicko who finds it fun and cloud stuff scares me LMAOOOO
@lyse@lyse.isobeef.org oh yeah i use the CLI sometimes it’s fun af
@kat@yarn.girlonthemoon.xyz Using full-blown Cloud services is good for old people like me who don’t want to do on-call duty when a disk fails. 😂 I like sleep! 😂
Jokes aside, I like IaaS as a middle ground. There are IaaS hosters who allow you to spin up VMs as you wish and connect them in a network as you wish. You get direct access to all those Linux boxes and to a layer 2 network, so you can do all the fun networking stuff like BGP, VRRP, IPSec/Wireguard, whatever. And you never have to worry about failing disks, server racks getting full, cable management, all that. 😅
I’m confident that we will always need people who do bare-bones or “low-level” stuff instead of just click some Cloud service. I guess that smaller companies don’t use Cloud services very often (because it’s way too expensive for them).
@prologic@twtxt.net yesss ty for listening and engaging with my kpop nonsense it’s really beautiful!
@prologic@twtxt.net i have seen some posts on this! that’s definitely reassuring. i don’t know cloud stuff at all and don’t want to. servers forever….
@kat@yarn.girlonthemoon.xyz UPDATE I DID IT!!!!!!! you will now see a cute anime girl that is behind the scenes testing if you are a bot or not in a matter of seconds before being redirected to the site :) https://superlove.sayitditto.net/
@kat@yarn.girlonthemoon.xyz think i’ll wait and see if the caddy module proposal gets anywhere bc that sounds like it’d make my life easier lol
@prologic@twtxt.net oh yeah it’s absolutely epic i love how fast it is. it would be extra peak if it sent a message to every bot that it denies access to that just says “get fucked” or something idk
@bender@twtxt.net Yeah, as you mentioned in the other thread, @andros@twtxt.andros.dev’s hashes appear to be not quite right. 🤔
@kat@yarn.girlonthemoon.xyz I guess we all whish we were jobless. Not moneyless, just jobless. 😅
@andros@twtxt.andros.dev Can you reproduce any of this outside of your client? I can’t spot a mistake here:
$ curl -sI 'http://movq.de/v/8684c7d264/.html%2Dindex%2Dthumb%2Dgimp11%2D1.png.jpg'
HTTP/1.1 200 OK
Connection: keep-alive
Content-Length: 2615
Content-Type: image/jpeg
Date: Wed, 19 Mar 2025 19:53:17 GMT
Last-Modified: Wed, 19 Mar 2025 17:34:08 GMT
Server: OpenBSD httpd
$ curl -sI 'https://movq.de/v/8684c7d264/gimp11%2D1.png'
HTTP/1.1 200 OK
Connection: keep-alive
Content-Length: 131798
Content-Type: image/png
Date: Wed, 19 Mar 2025 19:53:19 GMT
Last-Modified: Wed, 19 Mar 2025 17:18:07 GMT
Server: OpenBSD httpd
$ telnet movq.de 80
Trying 185.162.249.140...
Connected to movq.de.
Escape character is '^]'.
HEAD /v/8684c7d264/.html%2Dindex%2Dthumb%2Dgimp11%2D1.png.jpg HTTP/1.1
Host: movq.de
Connection: close
HTTP/1.1 200 OK
Connection: close
Content-Length: 2615
Content-Type: image/jpeg
Date: Wed, 19 Mar 2025 19:53:31 GMT
Last-Modified: Wed, 19 Mar 2025 17:34:08 GMT
Server: OpenBSD httpd
Connection closed by foreign host.
$
@kat@yarn.girlonthemoon.xyz i could build that myself but also i can’t because i don’t know code!!!!!!!!! her ass only knows ruby on rails!!!!!!!!!
@movq@www.uninformativ.de ancient……. i love old linux it’s so janky